Left of Post
Welcome to Memetic Warfare.
There were some surprise developments last week that made me push up some big reports, so we’ll get right to it. Today we’ll be looking at new reports from Anthropic, Recorded Future and two reports on residential proxies.
Firstly, it’s great to see Anthropic get into the TI game for real this time with their latest report:
I’ll share some of the high-level findings below:
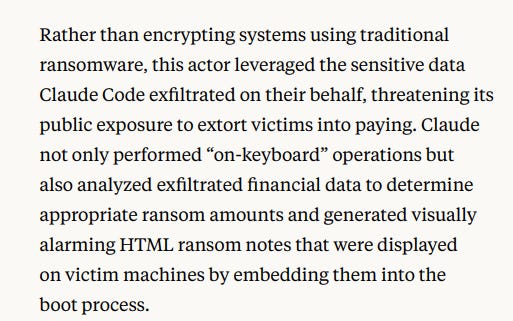
The report comes out of the gate strong with one highly-publicized case about a group using Claude to carry out “vibe hacking” successfully against 17 different victims:
Whatever security measures Claude had, which have been known to be very, very (if not too) stringent in the past, were not sufficient to prevent some pretty overtly bad stuff that should have been caught with prompts:
So, leaving the custom malware development and mas scanning that Claude developed aside, what struck me also was the use of AI post-infiltration - making the most of the compromised data to engage in negotiations more effectively. This, of course, could be just as easily applied to regular intelligence collection.
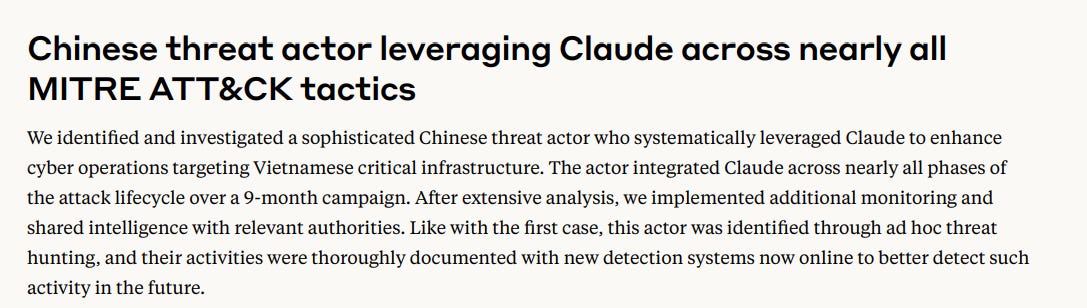
We’ll skip some other very interesting cases to get right to the legally-mandated Chinese APT usecase:
They truly get it and use AI for everything:
This is also the most specific we get so far for attribution and victimology, I guess Anthropic isn’t as concerned about getting detailed about Chinese activity:
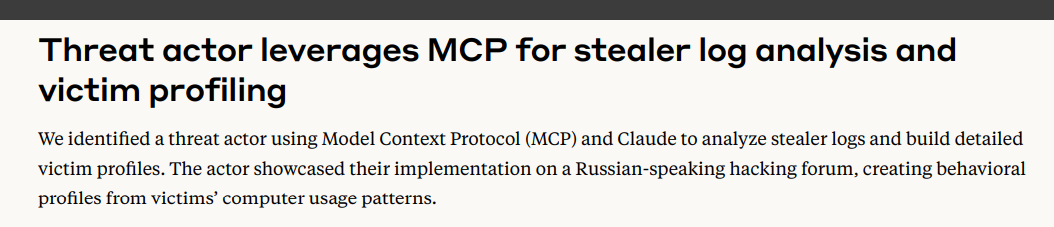
The most interesting use case IMO was the stealer log analysis and profiling case. One threat actor used claude with MCP to create detailed case files on individuals based on stealer logs - truly, a very interesting use case here.
In terms of espioange/intelligence collection, this is the closest we can get to a 1-1 case of applicability. Imagine the utility of doing this on hundreds of thousands of stealer logs or millions or much larger breached data databases.
They also get credit for a very brief “Implications” section.
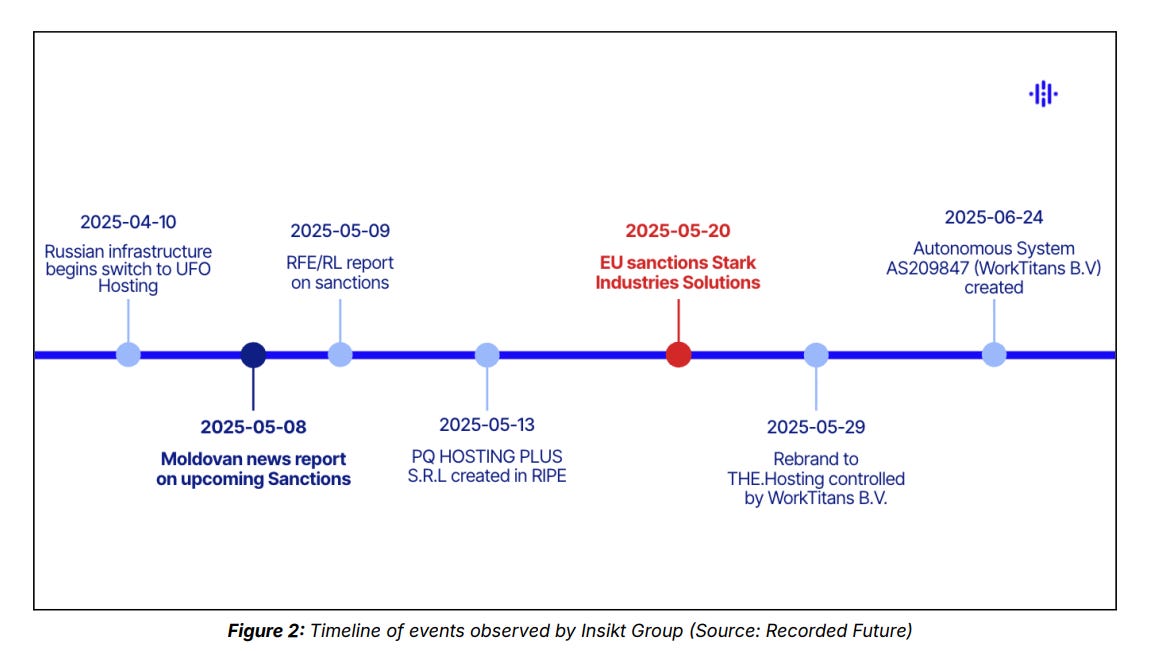
I also recommend checking out Recorded Future’s latest report on Stark Industries avoiding sanctions, available here.
Check out the key findings:
There’s a lot of detail, so I’d recommend reading the full report, as well as some solid graphics:
The most important element here is the continued focus on infrastructure. Most IO researchers focus on networks of bots, and if we’re lucky, they look at some domains. In practice, this is highly limited and misses the entire infrastructure that underpins these activities. If we want to get “left of post”, we need to be looking at ASNs, infra providers, proxies and more.
For any analysts reading, this is also a great opportunity. Read the report, learn about BGP and peering and how the internet works, and try to recreate the findings via tools like bgp.tools, Hurricane Electric and so on, and also - familiarize yourself with corporate registries.
Continuing our trend of looking at the foundational infrastructure needed for cyber/IO, I”m going to shout out two reports on proxy services from Spur and Infrawatch.
They’re both great, but I want to shout out the Spur research in particular for really diving in deep on how to use IP and domain information for attribution and investigation - give them both a read. Residential proxies are a critical service for cyber and IO, and I hope that we see more people looking at them holistically going forward.