Houthi MW Small Group
Welcome to Memetic Warfare.
The first order of business this week is to check out the latest report from friend of the blog and handsome man-around-town Max Lesser of the FDD, who collaborated with AJ Vicens of Reuters (also a fantastic journalist to follow) to investigate and expose a Chinese espionage network targeting laid off federal workers, available here.
The next order of business is the US ODNI Annual Threat Assessment available here.
I usually cover this in-depth, but frankly there isn’t a ton that caught my eye, so I’ll leave it to you.
Anatomy of a FIMI Incident
Now to the real topic of this week: the European External Action Service’s latest report on what is perhaps the worst acronym in the game, FIMI.
The report is available here. While I am an unironic FIMI hater, there are some good things in the report to bring up as well as some things that I love a bit less to say the least.
Let’s start with the table of contents. The report covers the Fimi “matrix”, but in terms of threat actors only covers Russia and China. Why isn’t Iran or any other actor mentioned? At the very least Iran should be, and it’s weird and frankly unprofessional that they aren’t.
Long time blog readers may recall that this is the third in a now longrunning series of reports:
As always, I’ll share the executive summary. Not much that you wouldn’t expect - elections, ”FIMI incidents”, AI and so on.
Unfortunately, I think that the very structure of the report is flawed. The report bases its claims off of research in 2024 finding over 500 “FIMI Incidents”, which is simply a highly limiting method of viewing the problem, as it’s impossible to cover events comprehensively or even to a significant degree. The lack of Iran and other actors further drives that point home - a huge percentage of total events aren’t even considered if they aren’t from Russia or China.
Let’s look at the main points they make based off of this:
The points here further emphasize the failure of the report to actually cover the topic holistically. Iran was very active during the Olympics but no mention. Romania isn’t mentioned - perhaps as it isn’t fully understood, but regardless, it should be.
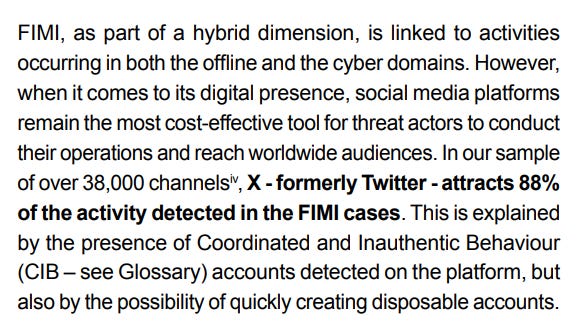
It gets worse though. The report claims that 88 percent of activity detected occurred on Twitter. Firstly, I never believe these stats, but this is a textbook case of selection bias. They are looking at Twitter for the most part as it’s the easiest platform to work on, so of course it’s most of what they see. No way is Twitter actually 88 percent of “FIMI” activity by itself. This also shows how events are a poor metric - an event is a vaguely defined occurrence, when much IO activity doesn’t occur as a specific “event”.
We get a big section on Russia:
And another one on China:
The above sections don’t give us much new information, but still nice to have centralized.
The next section tries to, in classic European fashion, provide a framework for understanding “FIMI”. This framework is underpinned by the meme iceberg seen below. We absolutely need a moratorium on the use of icebergs as metaphors in IO/cyber going forward.
The above iceberg I frankly don’t love as it’s simplistic - as frameworks and theories are in practice.
There’s also an attempt to map out “entities”, which without Iran is frankly silly:
The next section plays digital cartographer, mapping out network analysis of various operations. While I’m in favor of tracking cross-operation activity and activity in general, this is a highly limited attempt.
I get what they’re going for, but honestly, it’s just a waste of time. The below graph doesn’t show anything of value: what are we supposed to understand form it below? Additionally, it’s so limited as a graph that any findings that we could potentially glean would be unreliable.
What I thought was a bit better was the visualization of several “incidents”, which is a solid approach to use.
The report covers multiple known and active operations also, which is nice but not much value added.
The network graphs prove to be useless throughout the report, but the Chinese section at least includes one new finding.
That new finding is a new Chinese PR firm, which they titled “Volume News”. Hope that we get a writeup of this cluster one day! I’d even settle for threat indicators.
Lastly, we have the conclusions:
Overall, kind of boring and not much new, hope that that changes next time.
We’ll conclude this week with a podcast recommendation from one that I’ve recommended many times - 3 Buddy Problem. This week’s episode has some fascinating coverage of cyber-enabled IO from various actors