Hosting of Ill-Repute
Welcome to Memetic Warfare.
My name is Ari Ben Am, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also do training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
First order of business - I occasionally do public-facing training, and my next session on technical and qualitative attribution in IO is coming up on June 24th in Singapore! If you want to join, reach out via my contact information below.
Alongside that, I’ll also be running an OSINT course in Singapore with no specific emphasis on IO, but rather research, intelligence and investigations of all kinds.
If any readers in Singapore want to join or meet up when I’m there, just let me know via LinkedIn or via ari@telemetryapp.io.
As a quick Telemetry update as well - after a short break we’re back to large daily uploads of data, so if you haven’t checked it out recently - give it a try!
Sec-quoia
Let’s start today with more Doppelganger coverage. Sekoia recently published a very lengthy report on Doppelganger, available here. I’ll summarize the key findings.
The first, and one that is somewhat unsurprising all things considered, is that Sekoia found a ne Russian-language cluster, which they believe is part of a domestic propaganda campaign in Russia.
So far, pretty understandable. The next findingw as the adoption of CloudFlare as a CDN to obfuscate their host IPs:
Very nice of Sekoia to share their CloudFlare bypass technique, unsurprisingly utilizing a WordPress oversight, to find the host IP:
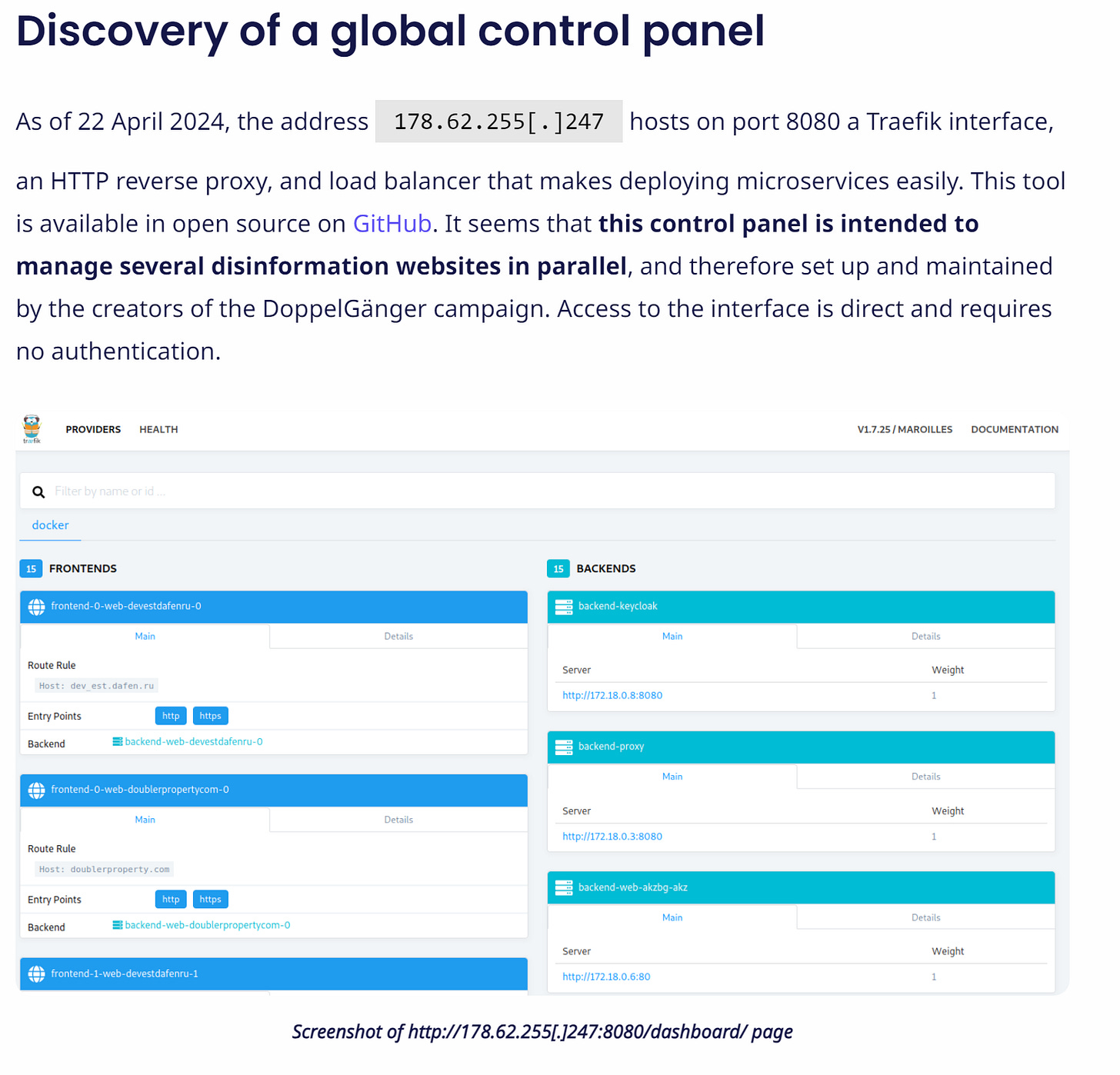
Sekoia didn’t disappoint also as arguably the biggest contribution of the report is further work on the “global control panel”.
The network set up an HTTP reverse proxy to facilitate incoming HTTP requests without exposing the final host. See CloudFlare’s description below:
This also has additional upsides as Sekoia states, but most importantly it makes it easier to operate and control various hosts via a unified control panel:
This is an interesting development and brings up a few points:
DoppelGanger’s operators, who have already been identified (at least partially) are unsurprisingly becoming more sophisticated technically
Security and anonymity is increasingly important. They may have left the control panel exposed, but the HTTP proxy and use of CloudFlare shows that there’s an attempt here to be more anonymous.
Scale is also a key concern - the use of a load balancer and the reverse proxy are indicative of that.
Overall, a very interesting finding and looking forward to the next one.
Hosting of Ill-Repute
The next topic that we’ll review is Krebs’ latest article on Stark Industries web hosting, available here. Krebs articles are always worth looking at, especially those that provide investigative methodology.
Krebs gets right to the point and summarizes the article well:
To summarize, Stark Industries is apparently a central provider of hosting services for cyber attacks and influence operations against “enemies of Russia”.
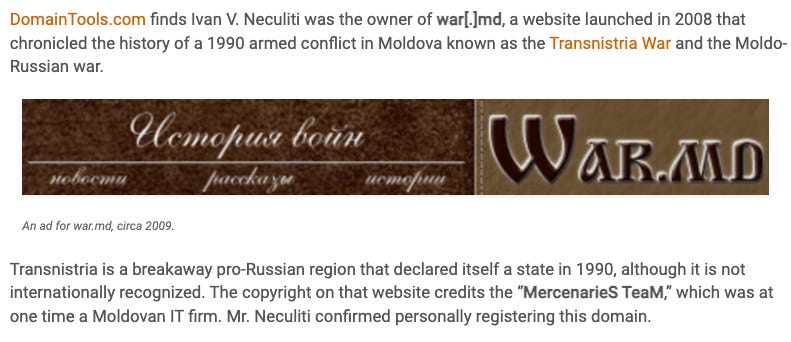
Stark Industries and its proprietor, Ivan Vladimirovich Neculiti, are quite interesting to investigate, and Krebs does a great job of looking at them, beginning with - what else - the UK Company House:
Following up on the name with a historical reverse WHOIS query, finding that Neculiti has registered a domain focusing on the Transnistria war.
Neculiti seems to have been inspired by the Elder Scrolls III Morrowind bold “Brown 2-ways” colorscheme.
Neculiti-var, as I will be referring to him throughout the rest of this article due to this color choice, registered it under “MercenarieS TeaM”.
Checking additional WHOIS records under Neculiti-var’s name also lead to his email address, as identified by Krebs as well. Checking that and other identifiers, which you should read about in the article, lead to this impressive flow chart of identifiers:
There’s even more discussion of the proprietor and his brother, but let’s move on to what ends Stark Industries is actually used.
The article refers to a Correctiv article that makes the below claims:
MIRHosting is also mentioned as a partner of Stark Industries, and itself has been utilized by Russian operatives in the past as per the article:
Notably as well, Stark Industries’ ASNs also appear to have been primarily Russian ranges:
Stark Industries, understandably, denies these claims, and their complicity in any alleged or otherwise illegal activity has yet to be proven conclusively, but Krebs’ claims are certainly interesting and are worth considering.
Why do I bring this specific case up? Well, in addition to simply being an interesting article with good investigative methodology, it’s representative of the ongoing trends that we will see more and more of in the cyber and IO space.
Hosting infrastructure is critical to carrying out cyber and influence operations. There’s no other way to effectively and semi-anonymously host domains, create accounts and operate online without using commercial hosting providers, or alternatively setting up your own.
Setting up your own has risks - it’s easy to misconfigure, it can be easily identified and then banned, and it’s easy to pivot on, thus exposing even more infrastructure.
Threat actors often choose to utilize certain hosting providers that are easier to exploit. Reputable hosting providers often have KYC requirements, are cooperative with LE, and even actively look to take down exploited infrastructure on their end.
Hosting providers of ill-repute, however, can be given low reputation scores and even be blacklisted by platforms and providers at the ASN level. This means effectively that any domains hosted on them would be viewed more suspiciously, if not be outright banned, from many online platforms.
As such, having effective proxies and the ability to set up hosting infrastructure via those proxies in a way that seems legitimate is critical. This is especially relevant as the world becomes less globalized, and increasingly localized internets pop up - the RuNet, the Great Firewall and so on.
The days of easily accessible, universal infrastructure seem to be coming to an end, and as such we may see more new potential proxy hosting services pop up in the future.
That’s it for this week! Follow the blog for more weekly posts and check out Telemetryapp.io!