Hack-and-Leak Elegy
The call is coming from inside the Keitaro instance
Welcome to Memetic Warfare.
I’m Ari, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
Let’s start off with a big week for Microsoft and their election security update. From there, we’ll cover a new and especially interesting Doppelganger report.
Firstly, Microsoft deserves credit for publishing regularly, unlike some platforms. This report has received a ton of attention already, so let’s skip to the parts I found most interesting.
There are some nice infographics on past activity, if a bit basic:
While a great infographic, I’d love to see a bit more detail. Look below for example - more background on what exactly is going on here would be fantastic.
Always great to see IO/cyber reporting combined, as Microsoft does:
Where it gets interesting is the exposure of an Iranian network of news sites targeting Americans:
Interestingly, Mandiant took notice of one of the domains back in 2022, but apparently never published on the other domains to the best of my knowledge?
Unsurprisingly, Russian actors are active:
The most notable section is on the following page. Rybar, the well-known Russian military blogger outfit, apparently has its own Microsoft Storm nomenclature and runs operations beyond the main Rybar channel:
TEXASvsUSA is out there wildin’ and makes sense - Russian actors historically just haven’t been able to not mess with Texas and continue to promote “Texit” narratives.
China gets a shoutout with Spamouflage activity:
Let’s go back to the Iranian operation, which IMO by far the most interesting. It’s a targeted, high-quality (comparatively) and long-term operation, showing more sophistication and planning than many would have attributed to Iran. Having looked at Niothinker, it’s one of the more impressive domains I’ve come across recently.
Bonus points for adopting the BRAT lime-green color scheme and being so far ahead of the curve! Very forward thinking of the IRGC.
Narratively it lines up with what you’d expect:
I may have some more coming out on this sometime soon so I won’t go into much more depth, but if that happens I’ll update you all here.
That’s not all of the big, presumably Iran-related news on the US elections this week though! The Trump campaign had internal documents that were hacked and sent to Politico and the Washington Post:
These documents included a 271 page vetting document about JD Vance, sent from one “Robert” using an AOL account, which is the most serious crime in this story. I’m just imagining having to subpoena AOL in the year of our lord 2024.
As a side note and pointed out by Kevin Collier, Guccifer utilized a hacked AOL account, which may be what happened here.
From here, “Robert” refused to speak on the phone (smart choice to avoid exposing accent), but offered other material.
But wait, there’s more:
The Trump campaign has stated that it may well be Iran behind the hack and leak:
Shortly after this, Trump himself blamed Iran for the hack and leak.
So there are some things to keep in mind here, as it’s still early. Whoever did this will want to get it out there. Going to newspapers with some form of reputation/basic ethics was probably a bad choice in that they thought twice about publishing the leaks.
Other journalist leads from reputable outlets may think twice now about this now that it’s been broken, so we may see the documents get leaked on 4chan, Telegram or hacking forums. Platforms now have time to prepare though, so any future post of the document itself (not that anyone really cares about open-source oppo research) would be mitigated more effectively, so great job on the part of the operators there.
The call is coming from inside the Keitaro instance
And now for the report on Doppelganger you’ve all been waiting for from who else but the Bayerisches Landesamt für Verfassungsschutz, or the Bavarian Office for the Protection of the Constitution, or BayLfV as neither of those are particularly catchy. It may be a bit unusual for a state level office to publish its own report on foreign espionage/interference, but apparently this is par for the course for Bavaria.
Bavaria is, to the best of my understanding, a bit different than the rest of Germany, and as such their office for Office for the Protection of the Constitution operates more independently (but still closely) with the federal office. Their desire thus to publish their own report on DG is more understandable, I suppose, and for us it’s great. See the title page below.
The report is pretty long but you should read it here in the original German. Let’s review the points that I thought were of interest below.
The first potent potable that I enjoyed was the description of the servers rented. The authors provide the specific Linux distro and break it down simply. Breaking the two down into servers specifically for Twitter and Facebook, as they found, is also a great finding. Unsurprisingly, they found that DG operators would SSH in to the servers as needed to set up the Keitaro instance and panel.
But wait, there’s more! The authors were able to intercept traffic from IP addresses that directly accessed the instances, presumably by penetrating the servers and having direct access themselves to the servers. Did this require any form of actual hacking, were credentials available in stealer logs, or were there other ways to directly access the instance? I don’t know.
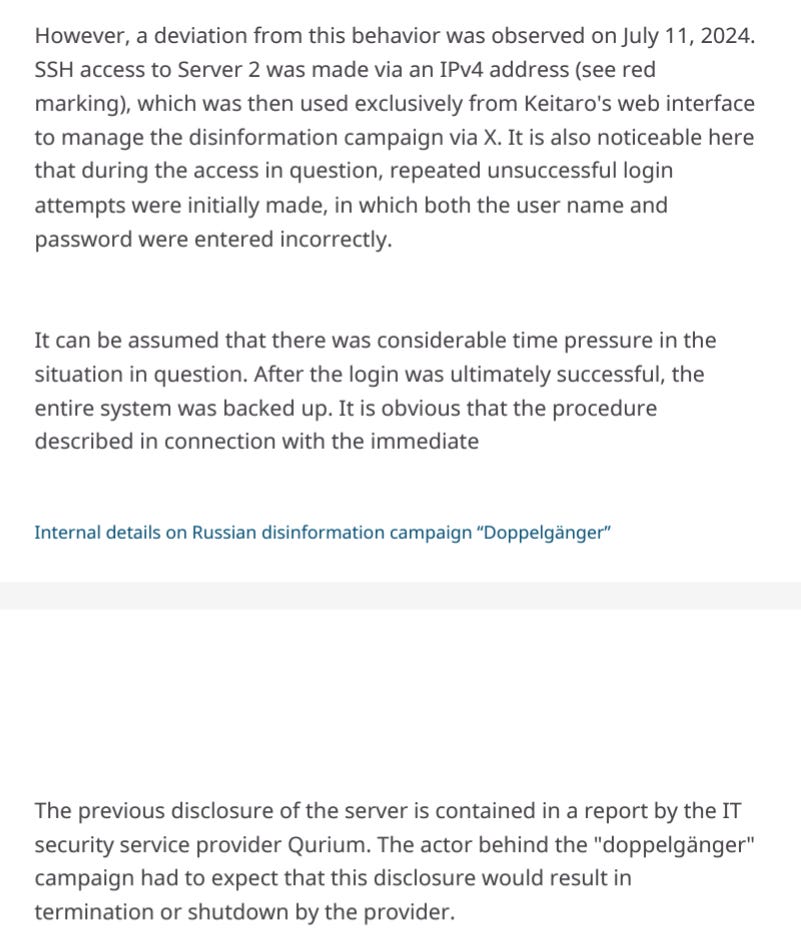
It gets more interesting. They specifically have the addresses of infrastructure that SSHed into the servers, so that’s further proof of direct access to the servers:
They even caught them backing up the servers following past Qurium reporting:
The report also contributes to the hosting company research done on Doppelganger, showing that some providers were used for Twitter or Facebook mostly.
There’s quite a bit more in the report, so if you get the chance, give it a read.