Guest Post: Skies of Blue?
Welcome to a Memetic Warfare guest post.
Occasionally I’ll post an article from a friend, colleague, or even someone with a different opinion from my own.
If you’re interested in having a post of your own shared on Memetic Warfare, please message me via the site.
As a disclaimer, all guest blog posts are the opinion of the guest author only, and Memetic Warfare does not endorse or have any stance as to the content of any guest post.
See below a guest post from friends of the blog Tuvia Gering (affiliated with the INSS, the Atlantic Council and Planet Nine) and Noa Rozmann of Planet Nine.
Darkening Skies: Bots and Political Disinformation on Bluesky
Since Elon Musk’s acquisition of Twitter in October 2022 and its rebranding to X by July 2023, a wave of Twitter-like platforms has mushroomed into existence. With much of X’s content moderation team axed, the platform has devolved into a hellscape of bots, disinformation, crypto-bros, and drop shipping spam, driving disillusioned users to seek refuge elsewhere.
While platforms like Mastodon, Meta Threads, Hive Social, and Substack Notes entered the fray with high hopes, they struggled to make a significant impact on the microblogging scene. However, following Donald Trump’s re-election in November, with ally Musk LARPing as “shadow president,” the microblogging platform Bluesky has emerged as a serious contender. By New Year's Eve, its user base had more than doubled to 26 million.
Figure 1: The number of social media accounts connected to the social media management platform Buffer from 2022 to 2024 shows that Bluesky and Threads have experienced rapid adoption, with the former “leading the charge.” (Buffer, Dec 12, 2024).
Launched in 2019 as an internal Twitter project under co-founder Jack Dorsey, Bluesky became an independent entity in 2021 with the ambitious goal of reinventing the wheel of social media. The platform looks and feels like old-school Twitter, with short posts, media sharing, and threaded conversations. What sets it apart is a free and open Application Programming Interface (API), which allows users, researchers, and developers unprecedented access to data and tools.
This openness encourages innovation reminiscent of Twitter's golden age, when tools such as Hoaxy, Botometer, and Tweepy enabled researchers to easily analyze and visualize information dissemination. It's a double-edged sword, though, as it also enables bad actors to take advantage of the platform by automating bot networks, stealing data, and training AI models without permission in an effort to target the spread of misinformation and speed up the dissemination of information operations. Perhaps sensing its potential, Chinese party-state mouthpieces have joined Bluesky, as have Russian state-run media outlets like RT and Sputnik, and in December, Eliot Higgins of Bellingcat identified the Kremlin-linked network "Matryoshka" as using Bluesky to spread disinformation about Ukraine.
In December Planet Nine's Digital Intelligence Team (DIT) used Bluesky's open API to develop automated scraping and analysis module. Using this module the DIT conducted an investigation, revealing another bot network, which it shared with Memetic Warfare. The network, referred to as "PortuBots," comprised at least 2,150 accounts that used Bluesky's architecture to spread spam and political content. Although Bluesky's Trust and Safety team successfully deactivated hundreds of these accounts, many remain active. The investigation also found other potential bot networks using the platform, which is outside the scope of this report.
Figure 2: Bluesky's User Growth Over Recent Months
(Sources: Bluesky, Jaz’s Bsky Stats, Statista, TechCrunch)
Using Planet Nine’s automated algorithms, we identified a few things about PortuBots:
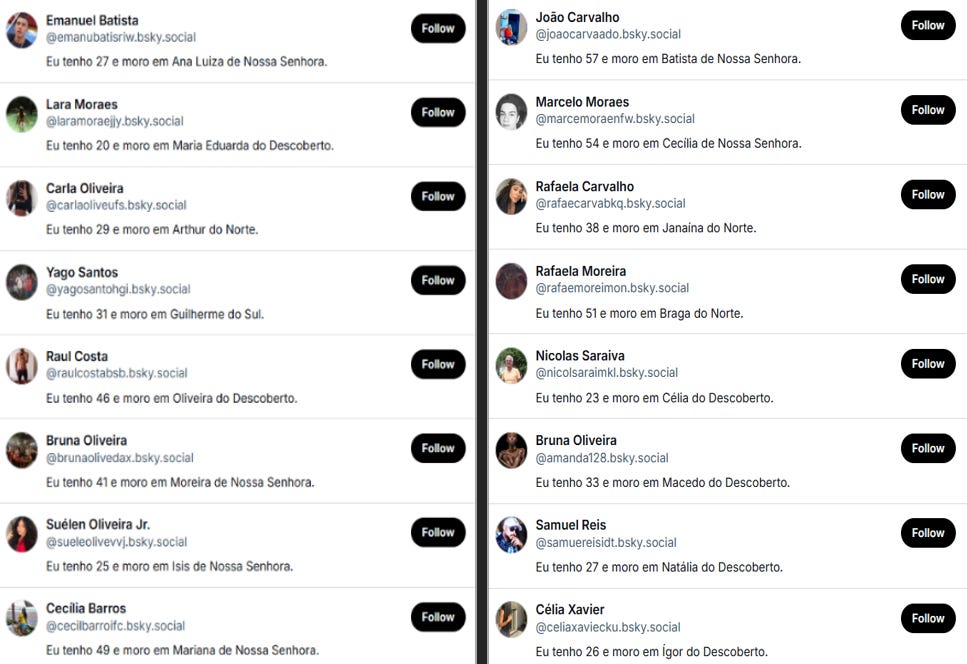
1. Portuguese bios - The bots’ bios follow a similar generic structure, with each starting with “Eu tenho” (“I am...years old”) and an age between 20 and 60, followed by “e moro em” (“and I live in”). Locations often include cardinal directions (“Norte,” “Sul”) or references from Portuguese internet culture like "Nossa Senhora" (“Our Lady”) and "Descoberto" (“discovered”). Some of the locations don’t exist, suggesting that AI was used to generate the bios and it "hallucinated."
Figure 3: A selection of PortuBots users and their bios
2. Repetitions – We observed that 330 out of 2,158 users in the "PortuBots" network had names appearing more than once, often with minor variations in handles, bios, and a different profile picture. 60 accounts with display names beginning with the honorifics "Dr." and 35 with "Sr.," most likely seeking variety or projecting authority and credibility.
3. High concentration of new accounts – Nearly all accounts in the PortuBots network were created within four days in early September 2024, peaking at 862 on September 1 before plummeting to just 9 by mid-December. This sharp surge and abrupt decline strongly indicate a coordinated bot network.
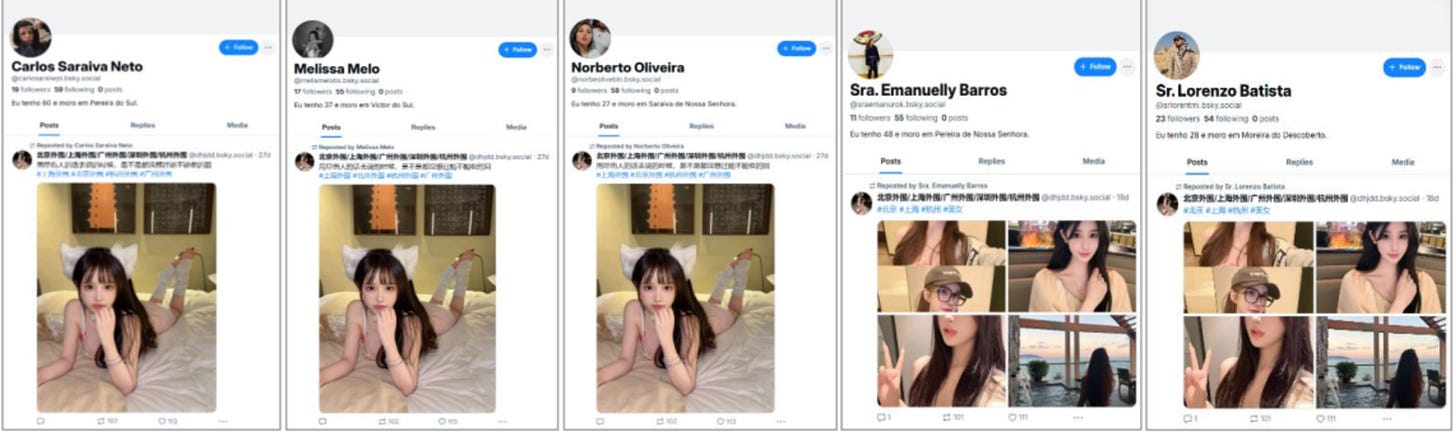
4. Mismatched profiles – There is often a stark contrast between the age stated in bios and profile pictures, with some users claiming to be 60 years old while appearing as young adults. Many photos are low-quality or blurry, and the absence of cover photos among most users further suggests inauthenticity.
Figure 4: Users displaying a noticeable mismatch between the age and their profile picture
5. Low connections, high engagement – On average, each user has approximately 15 “followers”, with the highest being 34 and the lowest 1. For the “following”, the average is roughly 58, with a maximum of 120 and a minimum of 13. This disparity suggests that while these accounts have limited reach, they actively engage with users outside the network, potentially amplifying the activity or visibility of specific users.
Key Narratives
Because of the limited activity of users within the network, as well as the wide range of topics they discuss, it is currently impossible to definitively attribute the bot network to any known threat actors. However, some narratives and TTPs are consistent with Russian disinformation:
· Criticism of Donald Trump and Elon Musk over their opposition to a stopgap spending bill gained traction, with at least 44 bots amplifying the message.
Figure 5: PortuBots users sharing a video criticizing Trump and Musk
· At least 60 users from the network reposted content first published in Chinese by user @dhjdd.bsky.social on December 2, 2024. The post featured a woman in revealing clothing paired with unrelated captions and hashtags.
Figure 6: Users sharing spam in Chinese
· In December 2024, Russia and Ukraine conducted a major prisoner exchange. On December 23, the account @rajawipu.bsky.social shared a fabricated Al Jazeera report claiming the Pentagon had criticized Kyiv. At least 52 users from the bot network shared this post. Fake citations of credible news outlets is a tactic consistent with "Doppelganger," the Kremlin-linked disinformation campaign. Notably, the post used the term "nationalist battalions," a phrase frequently employed by Russian state media and officials to portray certain Ukrainian military units as extremist or neo-Nazi to justify Russia’s illegal invasion.
· 52 bots amplified posts about Norway's Parliament extending abortion rights. Though factually correct, the sensitive topic sparked opposition from conservative and religious groups, and its amplification could deepen societal divides. Similarly, the network targeted France's political instability after the government collapsed following a no-confidence vote on December 4, 2024, suggesting the campaign's operators are attuned to divisive news across multiple countries.
· On December 8, 2024, @davidins.bsky.social posted an ad for the gambling site GGIEX, reshared by 104 users, including 54 from the network. While the geopolitical links are tenuous, the ad may target US gamers, previously dubbed "the backbone of right-wing trends" in Russian campaigns, or involve actors like North Korea, known for using gambling sites to earn hard currency.
Figure 7: Ads for online gambling
· On December 2, 2024, @solanafounder.bsky.social announced the release of a new Solana blockchain feature, with the post reshared by 122 users, including 57 from the network. While there is no evidence linking the accounts to state-sponsored campaigns, similar tactics have been observed on X by China-linked networks like "Spamouflage" to amplify propaganda, suggesting potential groundwork for future operations.
What Bluesky Can Do
On January 3, anti-bot activist antibot4navalny (@antibot4navalny.bsky.social) demonstrated the effectiveness of Bluesky's decentralized labeling system in combating disinformation campaigns such as Russia's Matryoshka network. The account launched a free in-app tool that allows for crowdsources tagging of suspicious posts and users linked to the network, with the option to "Warn" or "Hide" such content.
Bluesky’s default Moderation Service already offers a rich selection of tools to shield users from unwanted content. However, its effectiveness in safeguarding users and the potential implications for free speech remain difficult to evaluate at this stage.
Figure 8: User antibot4navalny’s tool for flagging and hiding Russian disinformation accounts.
While this approach opens up exciting possibilities for content moderation, it also raises concerns about potential abuse, such as overzealous labeling, censorship, or the silencing of dissenting voices.
In conclusion, Bluesky’s Trust and Safety team might consider strategies such as labeling state-run accounts to help users distinguish propaganda, identifying patterns like mass account creation and suspicious engagement, and providing affordable API access for researchers and non-profits.
Collaborating with the research community to develop tools for detecting coordinated inauthentic behavior and evaluating moderation efforts will be key, as automated tools like those used in this report can effectively uncover influence operations. Additionally, enhancing transparency and offering user-friendly moderation tools could empower the community and strengthen the platform’s security in the face of emerging threats.
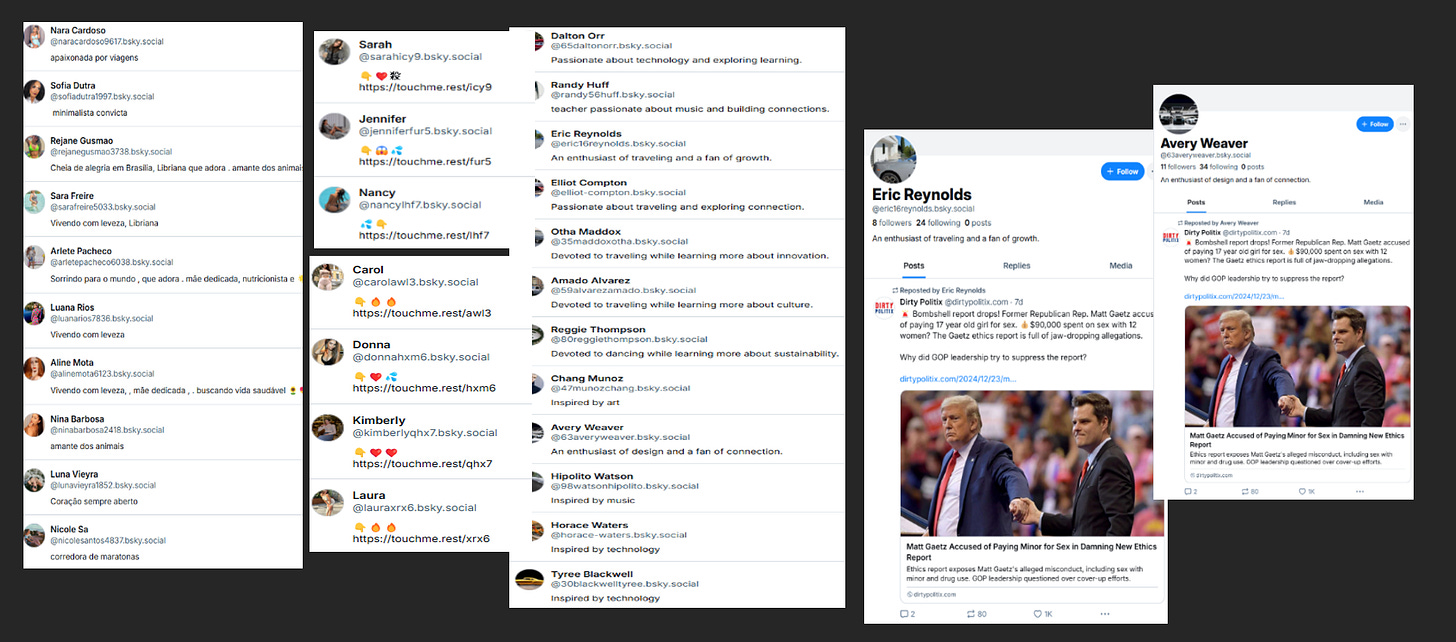
Figure 9: Other Possible Bot Networks in Bluesky
Note: The views expressed in this article are solely those of the authors, are based in good faith on the results of the described studies, and do not necessarily reflect the positions of their affiliated organizations. The data and facts presented in this article may not be accurate or complete.