Guest post: Suspected Chinese Virtual Espionage Network
Welcome to a special Memetic Warfare guest post from the FDD’s Max Lesser.
Max is a friend and colleague who has done some amazing work, and what he’s sharing here is the result of months of investigation he’s done into a sprawling suspected Chinese virtual espionage network.
Check out Max’s work below, and as always - guest posts are the sole opinion of the guest author.
All statements made here are made with the public interest and are the result of good-faith investigation. This post draws on publicly accessible technical data, domain records, platform metadata, and other open-source data. While the analysis identifies correlations and patterns, certain claims remain unverified and have not been formally established in legal proceedings. The findings should be understood as an evidence-based assessment of observable data, not a determination of wrongdoing.
Let’s begin.
Suspected Chinese Virtual Espionage Network Spans 100+ Websites
Hi, I’m Max Lesser.
Earlier this year, I uncovered multiple suspicious networks of websites representing apparently inauthentic organizations exhibiting behavior consistent with virtual espionage campaigns operating in line with Chinese geopolitical interests. This report identifies a much larger network of more than 100 websites displaying similar tactics, techniques, and procedures (TTPs) and pursuing similar targets.
This analysis involves no formal accusation of wrongdoing or criminal conduct on behalf of entities or individuals associated with the below websites. Organizations should conduct their own due diligence to determine whether each website may be malicious. If any company below believes they have been misrepresented, they can leave a comment and we will respond.
A journalist named Jacob Judah provided me with the initial lead for this network, focalpointstrategysg[.]com. The following techniques connected this website to the other websites in this network:
Identifying related domains hosted on the same dedicated web hosting servers
Identifying related domains hosted within the same IP ranges
Fingerprinting servers based on unique port/service configurations
Pivoting off of shared payloads in HTTP responses
The following sections provide an example of how each technique exposed websites in this network. I am describing the investigative techniques in efforts to aid the research community in finding related websites. I am also providing the list of websites at the end to help protect people and organizations from threats utilizing these websites.
Identifying Related Domains Hosted on the Same Dedicated Web Hosting Servers
Identifying dedicated web hosting servers associated with the domains in this network occasionally led to domains associated with websites displaying similar behaviors or sharing technical indicators.
The same operator(s) often control domains hosted on the same dedicated web hosting server. When a dedicated web hosting server currently hosts or historically hosted websites that exhibit similar features within a relatively short time period, this indicates likely networked behavior.
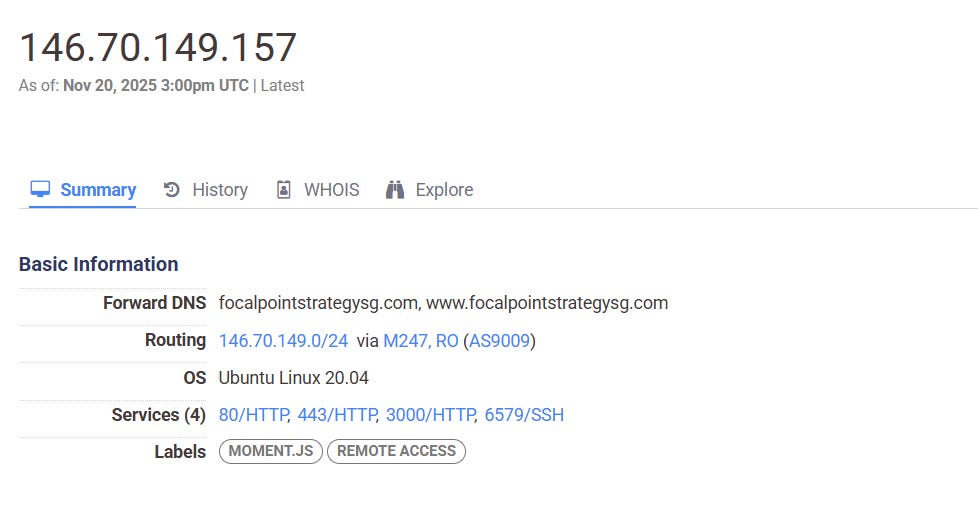
For example, 146.70.149[.]157 currently hosts focalpointstrategysg[.]com. The server appears to be a dedicated web hosting server. 146.70.149[.]157 also historically hosted anemoconsulting[.]com. Like focalpointstrategysg[.]com, anemoconsulting[.]com appears to represent an inauthentic consulting company based in Singapore.
Figure: Partial view of PDNS results from Validin for 146.70.149[.]157.
Identifying related domains hosted within the same IP ranges
Triaging domains in the IP ranges encompassing the IP addresses of dedicated servers hosting domains in the network often surfaced more websites in the network. Malicious actors often use web hosting servers within specific IP ranges because certain hosting providers have a higher tolerance for suspicious behavior or have more relaxed know your customer (KYC) policies.
For example, a web hosting server located at 146.70.149.157 hosted focalpointstrategysg[.]com, the initial lead for the investigation. This address falls into the IP range 146.70.149.0/24. Servers associated with IPs in this range hosted the following websites that exhibited similar features to other websites in the network:
Focalpointstrategysg[.]com (146.70.149.157)
Anemoconsulting[.]com (146.70.149.157)
Starexecadvisor[.]com (146.70.149.133, 146.70.149.176)
Gairesearchalliance[.]com (146.70.149.142)
Actionnowsg[.]com (146.70.149.166)
Widensight[.]com (146.70.149.181)
Bocconsultingpro[.]com (146.70.149.216)
Kwanhung-group[.]com (146.70.149.226)
Prohuntsingapore[.]com (146.70.149.227)
Movieplothr[.]com (146.70.149.248)
Verticalpeakonline[.]com (146.70.149.158)
Saconsultingglobal[.]com (146.70.149.253)
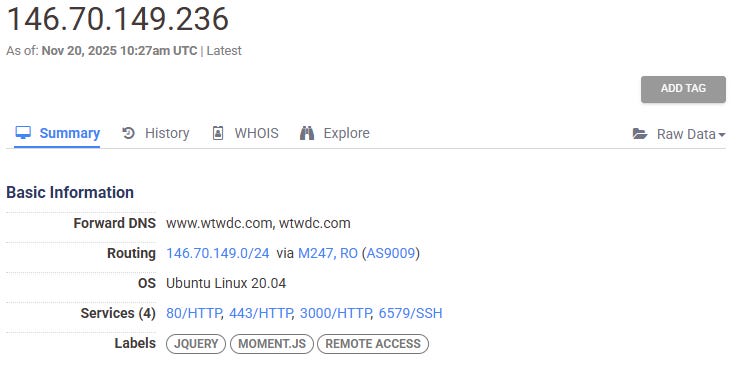
Wtwdc[.]com (146.70.149.236)
Chislonconsult[.]com (146.70.149.169)
lotyes[.]net (146.70.149.247)
Fingerprinting servers based on unique port/service configurations
Fingerprinting servers hosting domains in the network based off of unique combinations of ports and services, especially those involving nonstandard configurations, also surfaced related websites in the network.
For example, 146.70.149.157, the server hosting focalpointstrategysg[.]com, includes the following configuration for its services: 80/HTTP, 443/HTTP, 3000/HTTP, 6579/SSH. While 80/HTTP and 443/HTTP are standard port configurations, 3000/HTTP and 6579/SSH are nonstandard port configurations.
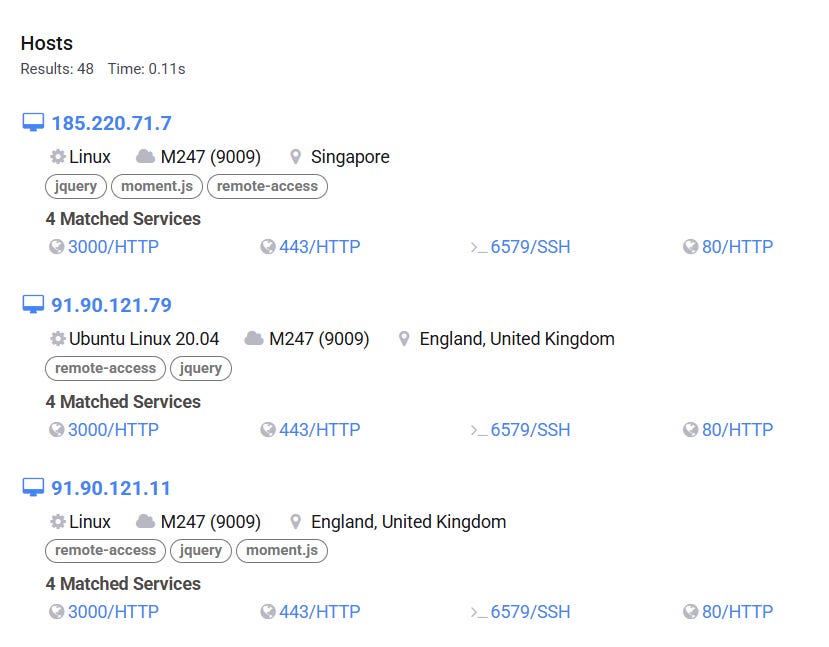
This makes the server’s configuration a unique pivot point that can surface servers with similar configurations, which will potentially host other sites sharing behaviors and technical indicators with the network. Searching for servers with this exact configuration on Censys yields 42 results as of November 20, 2025.
Figure: Censys showing port/services configuration of 146.70.149.157, the web hosting server for focalpointstrategysg[.]com.
Figure: Results from Censys query for servers with 80/HTTP, 443/HTTP, 3000/HTTP, 6579/SSH and only four services.
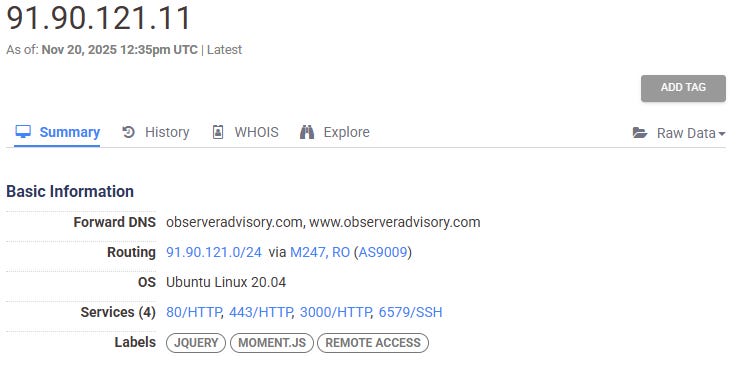
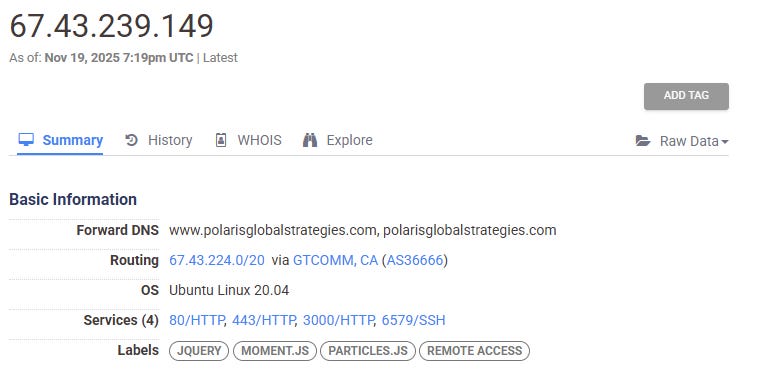
Many of these servers host domains with related behaviors and other technical indicators that connect them to the broader network. For example, the domains observeradvisory[.]com, polarisglobalstrategies[.]com, and wtwdc[.]com are hosted on servers with this same service configuration. The websites associated with these domains all appear to represent inauthentic companies.
Figures: Web hosting servers with the configuration 80/HTTP, 443/HTTP, 3000/HTTP, 6579/SSH hosting domains in the network.
Pivoting off of HTTP payloads
When a webpage loads, the browser retrieves content from the web hosting server through a series of HTTP transactions. These transactions often include metadata about the resources delivered, such as filenames, hashes, and request paths.
The platform URLScan captures these HTTP transactions and displays associated resources. By clicking on a payload’s name or hash, you can view other websites that load the same file.
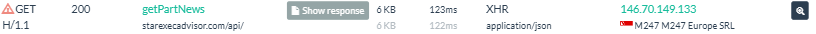
For example, one site in the network, starexecadvisor[.]com, included an HTTP XHR request to a payload named getPartNews, which can be correlated with other domains that retrieve the same resource.
Figure: URLScan capture showing payload named “getPartNews” in starexecadvisor[.]com’s HTTP transactions.
Other sites publicly scanned on URLScan that also retrieve this resource display behavior consistent with the network. As of November 19, 2025, a selection of these sites include:
pogconsult[.]com
publicserverfsgf[.]idfnv[.]net
eurosternconsulting[.]com
cairuift[.]com
maxwellconsultings[.]com
snokcitic[.]com
iajpl[.]org
starharb[.]com
teconsultingllc[.]org
chislonconsult[.]com
testavc[.]com
gogoglobalnow[.]com
starexecadvisor[.]com
sicconsultings[.]com
globalmarketsg[.]com
leadingfinding[.]com
dicwayua[.]com
The Network’s Connections to China
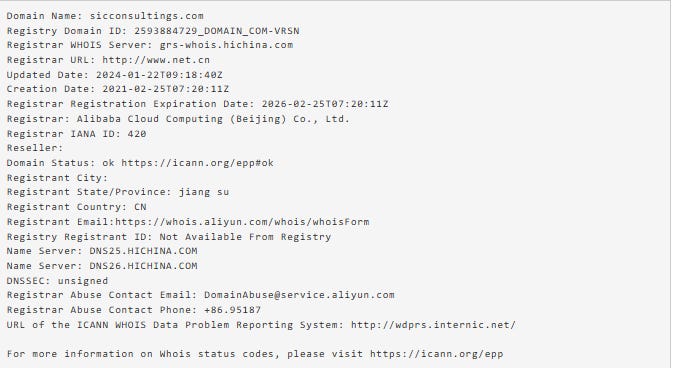
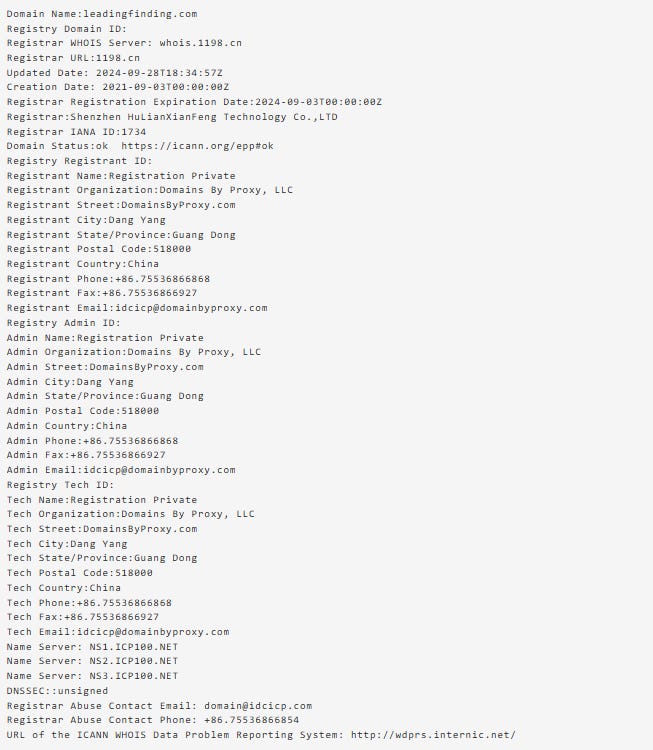
Though almost all of the websites in the network use privacy services that mask the identity of their registrants, WHOIS records for sicconsultings[.]com show Jiang Su, China as the registrant’s location. Leadingfinding[.]com, a website no longer online but which previously displayed behavior consistent with the network and shared technical indicators, also has a Chinese registrant and registrar.
Figure: WHOIS record for Sicconsultings[.]com from 2025-09-09.
Figure: Partial view of WHOIS record for leadingfinding[.]com from 2022-10-10.
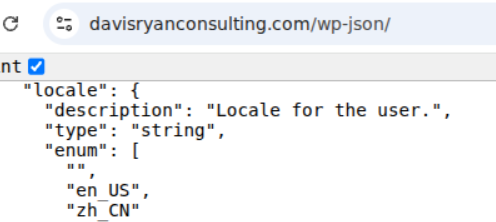
In addition, multiple websites in the network are WordPress sites that appear to have Chinese language packs installed for their administrative back end. A default WordPress installation only includes English (en_US), but a site administrator may add additional languages. The WordPress REST API exposes a field called “locale” for each user, and the available values for this field correspond to the language packs that are installed on the site.
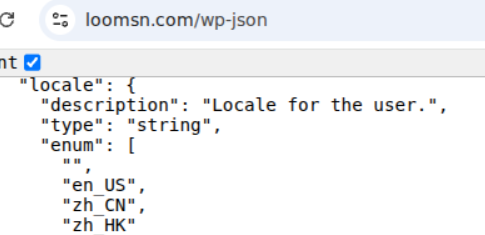
For example, both davisryanconsulting[.]com and loomsn[.]com include zh_CN as available values for “locale” for users, and loomsn[.]com also includes zh_HK. Davisryanconsulting[.]com describes itself as the website for a company in Boston and loomsn[.]com for a company in the United Kingdom and Germany. The fact that both sites include these languages as available values implies that the WordPress administrator added these language packs, which is incongruous with the listed locations of the companies associated with the websites.
Notably, these are not translation plugins for public-facing content, but rather language packs for the WordPress administrative dashboard itself, indicating that site administrators or content managers are likely operating the backend in Chinese.
Figures: Locale fields for WordPress users on davisryanconsulting[.]com and loomsn[.]com, showing zh_CN as an available option.
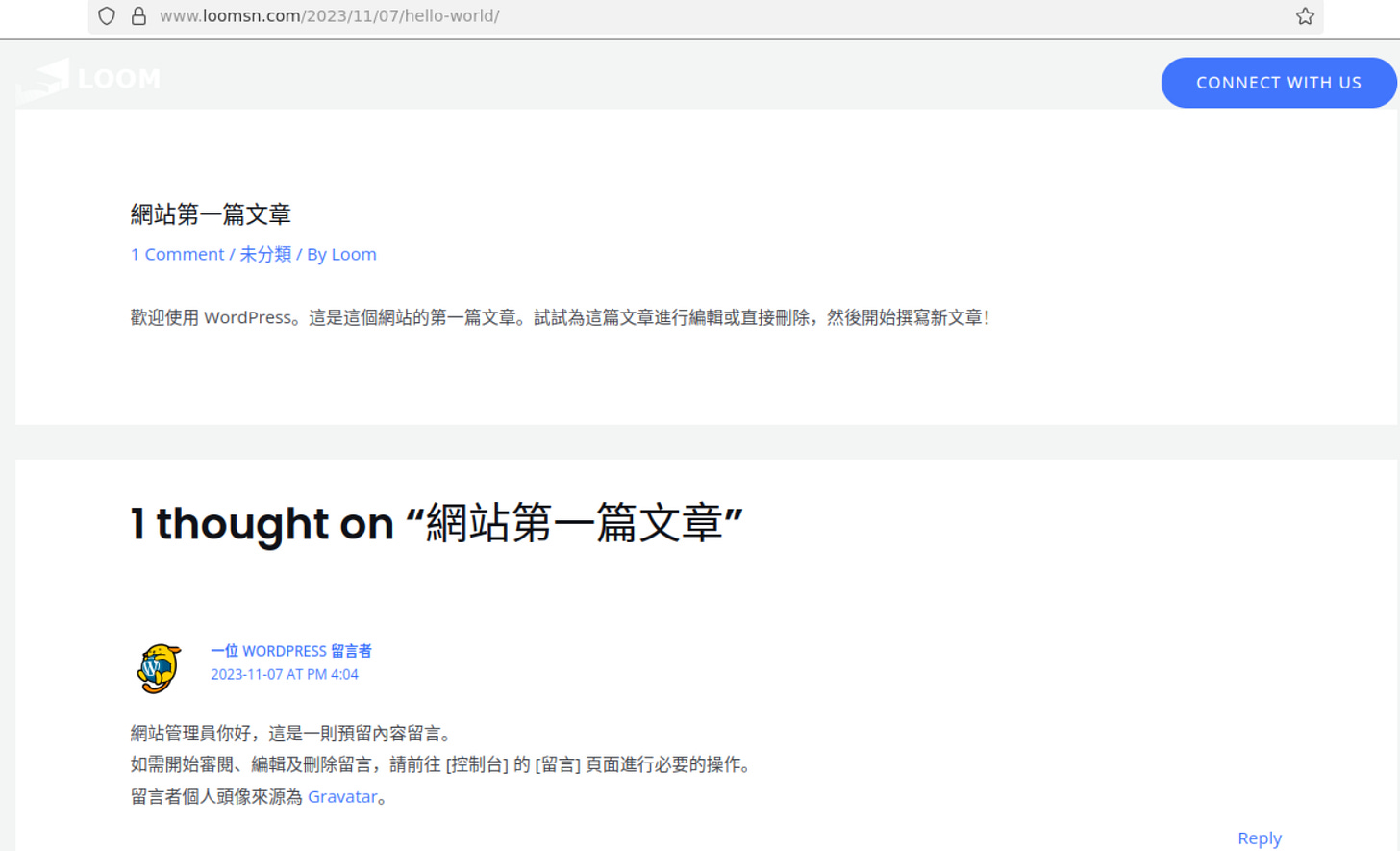
Loomsn[.]com also has a Chinese-language “hello world” page. “Hello world” pages often appear as default pages on WordPress websites.
Figure: Chinese-language “hello world” page for loomsn[.]com.
Full List of Suspected Domains in the Network
The below lists suspicious websites in this network. The list is not exhaustive and may include false positives. Some of the websites no longer appear online, but most are archived.
Though most websites in the network present themselves as consulting companies, some also impersonate risk-advisory firms, public relations and branding agencies, headhunting firms, media outlets, and even humanitarian organizations. Anomalies include a Chinese-language Singaporean news site, a military-enthusiast community, and a Macau-based casino company.
Across the network, the sites advertise services ranging from geopolitical and macro-policy analysis to cybersecurity, supply-chain resilience, investment advisory, and human resources recruitment. The majority of the companies claim to be based in Singapore, Hong Kong, or Taiwan, while others list offices in Malaysia, Shanghai, London, New York, Boston, Dubai, and Beijing, among other locations.
focalpointstrategysg[.]com
anemoconsulting[.]com
starexecadvisor[.]com
gairesearchalliance[.]com
actionnowsg[.]com
widensight[.]com
bocconsultingpro[.]com
kwanhung-group[.]com
prohuntsingapore[.]com
movieplothr[.]com
verticalpeakonline[.]com
saconsultingglobal[.]com
teconsultingllc[.]org
apcmsg[.]com
globalmarketsg[.]com
sicconsultings[.]com
wtwdc[.]com
chislonconsult[.]com
iajpl[.]org
starharb[.]com
leadingfinding[.]com
elitebridgeconsulting[.]com
ccnetadvisory[.]com
lightspot-consulting[.]com
woodfarmstrategy[.]com
observeradvisory[.]com
sicotaiwan[.]com
wisdintel-consulting[.]com
testavc[.]com
bsfintlconsulting[.]com
hyssenburglee[.]com
strategynexus[.]org
vistastrategyasia[.]com
mwbnconsulting[.]com
tradesyncsupply[.]com
elitecommunicationpr[.]com
global-scope[.]com
srccsc[.]com
gogoglobalnow[.]com
cgconnect[.]net
topviewconsultgroup[.]com
jetsoncheng[.]com
minshihconsult[.]com
sagavisionglobal[.]com
jgadvisorsus[.]com
lotyes[.]net
westeastern-consulting[.]com
navigatingconsulting[.]com
togetherwiseconsulting[.]com
harbourlandstrategy[.]com
asiafutureconsulting[.]com
oasisriskmanagement[.]com
pearlriseglobal[.]com
pearlriseconsult[.]com
hashwave[.]net
nimbushubconsulting[.]com
loomsn[.]com
elitecombathub[.]org
insightbridge-consulting[.]com
consultingtiktank[.]com
maxwellconsultings[.]com
xinbaonewssg[.]com
cairuift[.]com
davisryanconsulting[.]com
ryanconsulting[.]com
morningstar-uk[.]com
morningstarte[.]com
deeperworldconsultancy[.]com
shicsc[.]com
riskradarconsult[.]com
tentecon[.]com
talenthuntconsult[.]com
talentcentralhr[.]com
sunconsultingus[.]com
transpacifichk[.]com
insightful-edge-consulting[.]com
veritasrisksa[.]com
aps-consultinghk[.]com
pagodiancapital[.]com
valoripount[.]com
chinaoverseassecurity[.]com
241177[.]com
hgtintertrade[.]com
snokcitic[.]com
eurosternconsulting[.]com
invfront[.]com
deshengconsulting[.]com
jxtechcons[.]com
sparkelinternationalhr[.]com
publicpogconsult[.]com
dicwayua[.]com
tivitfinance[.]com
pogconsult[.]com
apsight[.]com
rimpac-sg[.]com
rechpulsehk[.]com
tradenovasolutions[.]com
globalizationhk[.]com
bizbeacon[.]org
britanniabizadv[.]com
polarisglobalstrategies[.]com
pinnaclehorizonconsulting[.]org
pacificgeocon[.]com
82insight[.]com




The fingerprinting techinque using nonstandard port configurations like 3000/HTTP and 6579/SSH is clever for uncovering related infrastructre. Pretty wild that so many sites in the network had Chinese language packs installed on the backend when they clamd to be US or UK based consulting firms. The zh_CN locale stuff makes it obvious somone was managing these from a Chinese environemnt.