Girlboss, Gaslight, Gatekeep 0days
Welcome to Memetic Warfare.
I’m Ari, and I’m the founder of Telemetry Data Labs - a Telegram search engine and analytics platform available at Telemetryapp.io. I also provide training, consulting and research so if you have any specific needs - feel free to reach out on LinkedIn.
Let’s start with a potential (suspected) Iranian influence operation talking about Israeli politics and affairs. This one, titled “Israel in a minute”, has spent some money on ads. Even better, they have a Linktree, saving me 5 minutes!
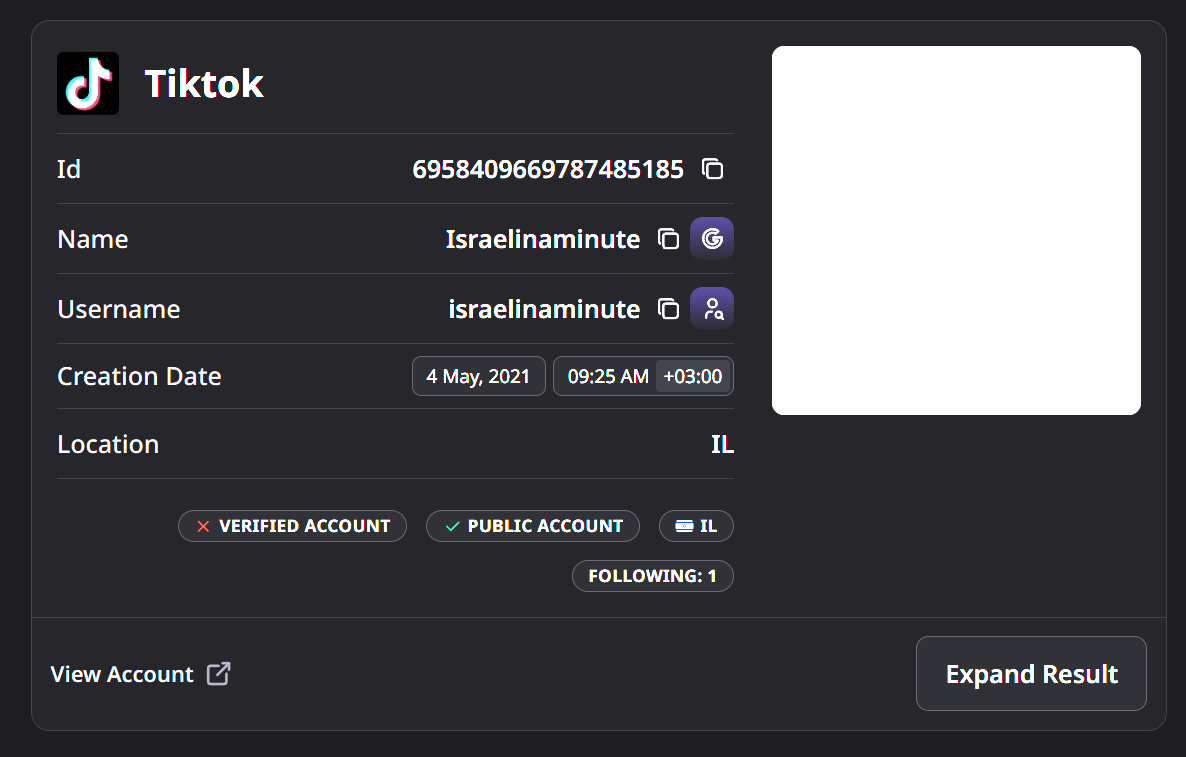
Let’s look through the various accounts below and see what’s up. let’s start with TikTok to get it over with.
The account was set up in the right geo - you’d be surprised how often this is an OpSec failure:
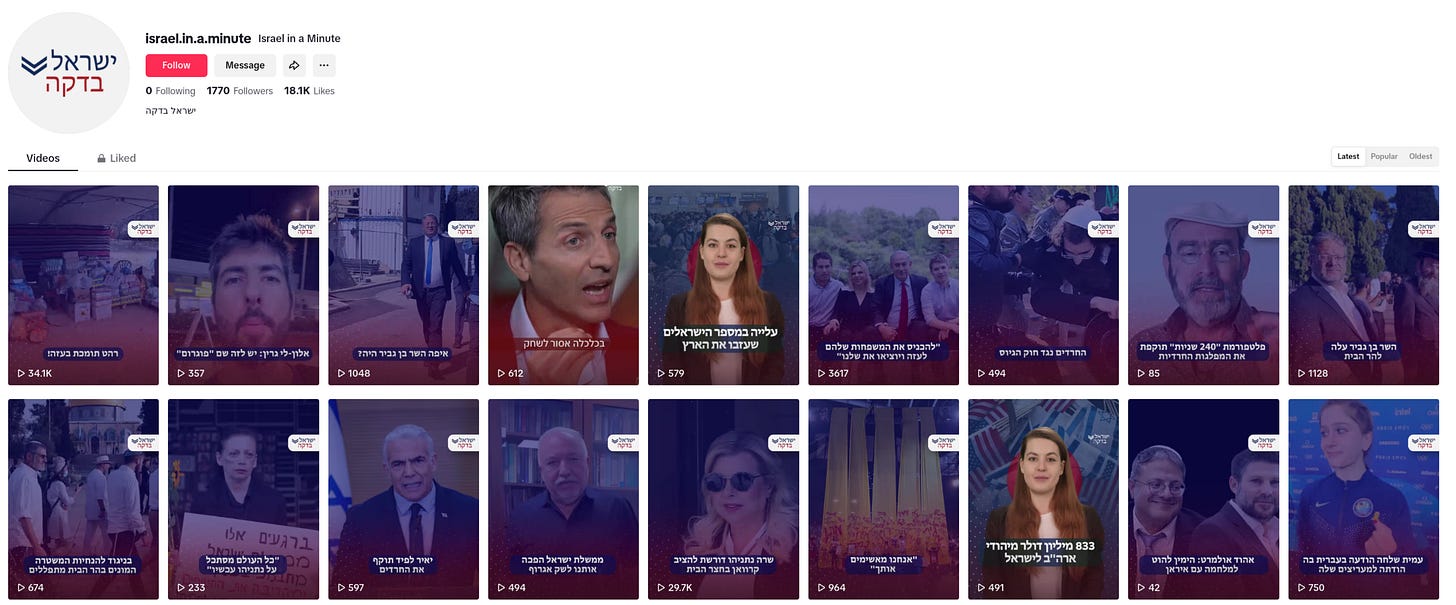
The videos are pretty indicative of what you’d expect.
Use of AI anchor:
Watching one of the videos confirms it:
There’s another one as well:
The average YouTube video gets a few dozen views, but a few have gotten over a few hundred:
The Twitter account is quite old and has probably changed names over time (maybe bought or hacked):
The Facebook and Instagram account are down unfortunately, so not much we can do there. I was able to get a quick look at them prior to them getting taken down, and they did run ads so presumably that was how they got taken down.
So, we have a domain of multiple accounts with no central domain trying to pass it off as a news outlet. This makes sense, and dropping the domain to me is a good idea to reduce opsec breaches. I’m willing to bet that the ads they ran are what got them taken down by Meta, but the other platforms haven’t caught on yet.
The use of an AI anchor is interesting but something that we’ve seen multiple times before. The network on the whole is reminiscent of “Dofek” but a slightly lower-cost version. Anyway, pretty straightforward and the kind of thing I’d expect to see more of soon.
Sepah’ on That
Iran has turned out to be the dark horse of election interference this election cycle - from running influence operation networks (more on this in a future post) to hacking Roger Stone’s email and trying to get US newspapers to publish oppo research on JD Vance.
Unsurprisingly, Iranian actors used generative AI in their operations shown by Open AI’s newest report.
The domain content isn’t bad at first glance in terms of quality.
Some AI-generated images were used to boost social media accounts. Good use of the “back facing the camera” trick! Makes it harder to identify as AI by avoiding the face.
That’s about it - just some more information here, and a new domain. Two questions though:
I wonder when we’ll see actors try to exploit other platforms such as Claude as much as they do ChatGPT, or if they already are.
Will we see Microsoft and Open AI joint reporting soon?
Nobody Expects the Q2 Adversarial Threat Report
Meta’s Q2 Adversarial Threat Report is now out, so let’s take a look at it. There’s a lot of Russia, so we’ll discuss that below. The report opens with some “key insights”, the first of which being the use of generative AI:
Is it just me, or did we as a community kind of get over the whole genAI threat discourse pretty quickly? Seeing far and far less of it in the past few weeks or even month or two after a ton of hype. It’s been problematic and surely will continue to be so, but for the most part in a comparatively predictable and straightforward way.
Some of the other key findings were frankly obvious. Russia is going to be carrying out operations on topics that are important to it, so Georgia and Moldova are big ones:
The for-hire operators trend is worth discussing momentarily. For-profit operators are nothing new, but increasingly for-hire operators are filling the role once carried out by government agencies. We may see a split in the future that becomes more pronounced between private companies doing the low-hanging fruit of spam operations whereas government agencies focus more on cyber-enabled IO, let’s say. This also will continue to be feasible Western relations with Russia get worse; attribution matters less as sanctions are the only real lever short of cyber attacks to counter private-firm IO in a country that doesn’t care about Western naming and shaming or civil legal action.
The next “takeaway” has also always been the case. We’ve always overblown IO, which is usually done poorly, to be some grander threat than it is in most cases. Additionally, one of my points has always been that discoverability and stat boosting is one of the inherent goals of most IO. The operator, be it a firm or government official, must show quantifiably how their effort does “something” to their higher-ups:
There’s some more, but let’s move on to the operations. The first targeted Georgia, Armenia and Azerbaijan.
This operation utilized a small number of online entities, but had a very solid budget for ad spend (which I still theorize is one of the key ways, if not THE key way, that Meta really monitors for IO on their platform). This lead was also reported originally by a Georgian NGO, a recurring trend here, and carried out by a Russian marketing firm.
Let’s go to number 3. This “3-D Chess” operation is actually quite interesting in that it attempted to weaken Ukraine “pretending to support it”. There’s a smattering of real world activity as well - stickers with QR codes to promote the network’s Telegram channel. I wonder if there’s any overlap with CheckFirst’s Matryoshka network, and the overlap with Doppelganger activity is also a notable point:
Let’s move on.
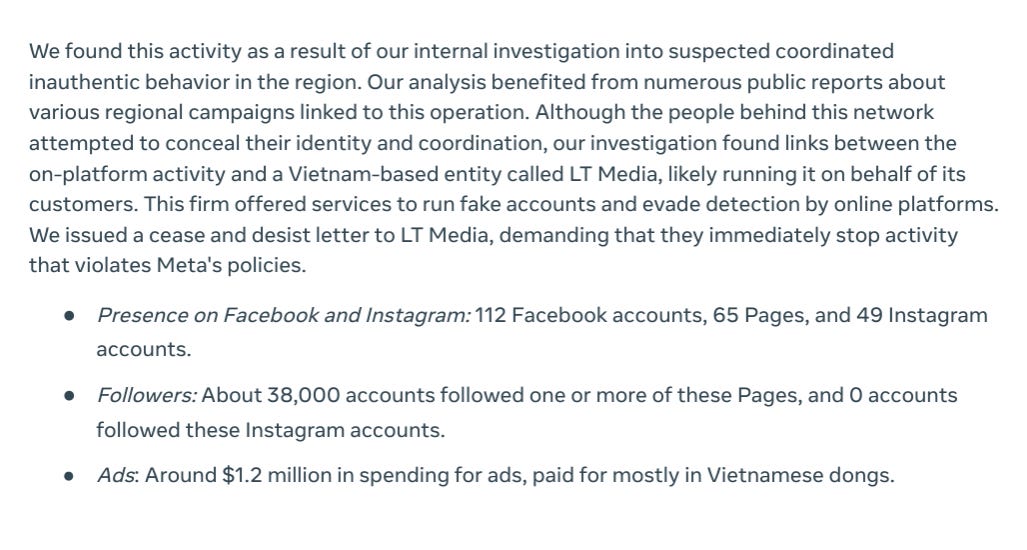
This case is interesting. The network has blown massive ad spending, but no attempt to attribute beyond the marketing company. This is probably the responsible thing to do, as if Meta had proof that it were Israeli (which it may not be, could be done independently by an independent funder, for example) they’d state it being as such.
Overall a solid report in total quantity and quality, but I think that some of the sections were a bit overblown (DG in particular).
And Now for Something Completely Different
Recorded Future’s latest election security report is now available and I’d highly recommend checking it out, as always. There’s coverage of “Empire Dragon” (Spamouflage) and other activity, including one particularly interesting network called Hoopoe.
There may be some more coming out on this soon, so be sure to follow future issues of Memetic Warfare.
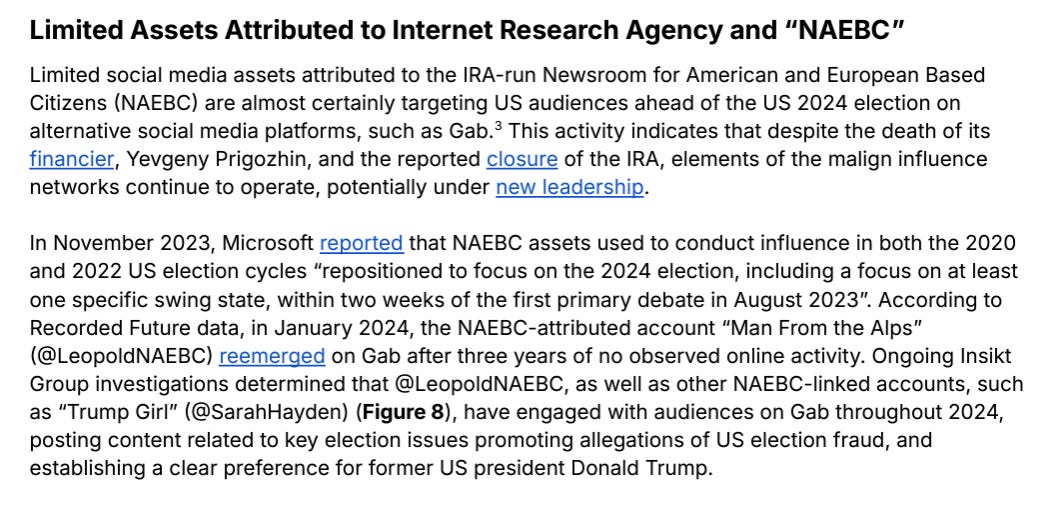
One of the things that I enjoy about RF reporting, alongside the overall high-quality and technical detail, is their comprehensiveness in viewing the landscape as a whole. This is one of the upsides of not being a platform-specific team, and it shows. Being able to track ongoing campaigns across various platforms effectively is a big upside, and I give them credit for tracking even previously exposed campaigns persistently - see below:
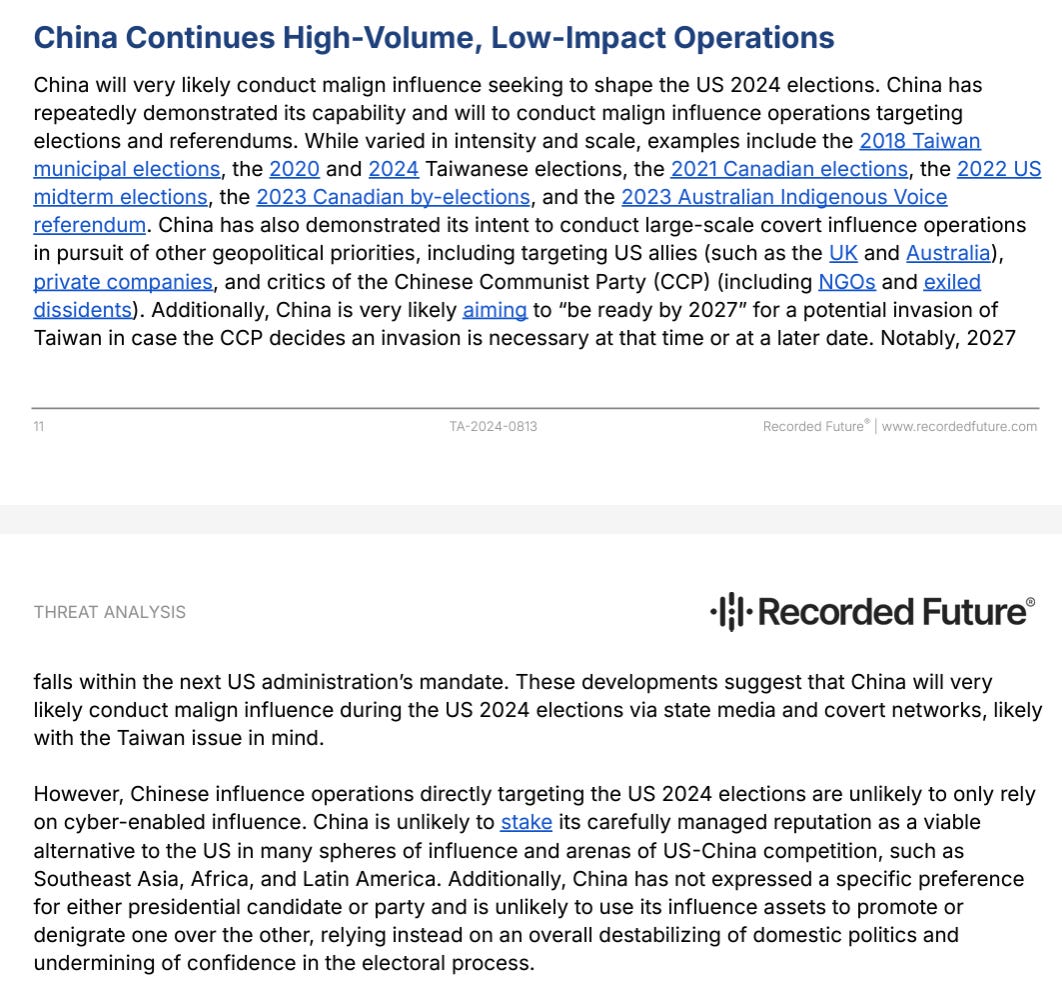
Interestingly, RF seems to disagree with the ODNI claim that China probably won’t interfere in the US elections:
See the ODNI’s prediction:
This may be just a different way of wording it - perhaps that China doesn’t see a need to boost or take down a particular candidate, but either way I think that RF is more on the money here than the ODNI is.
Girlboss, Gaslight, Gatekeep 0days
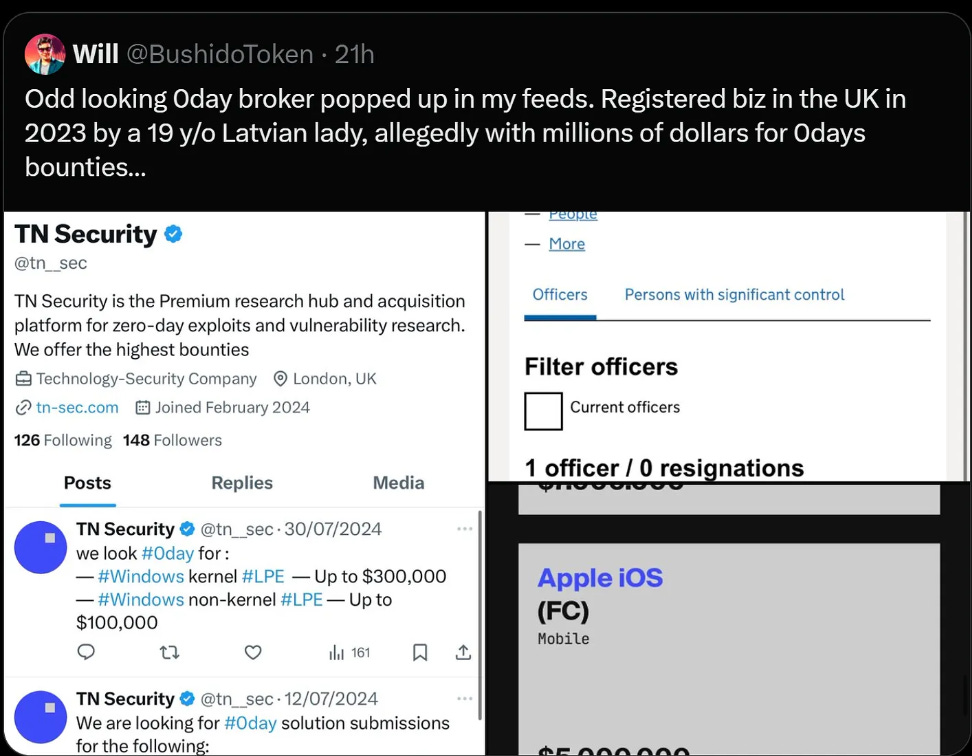
Remember TNSECURITY from the Qurium report on Doppelganger and Russian bulletproof hosting services? Well, they’re back thanks to Bushido Token coming across some suspicious activity from their UK registered front:
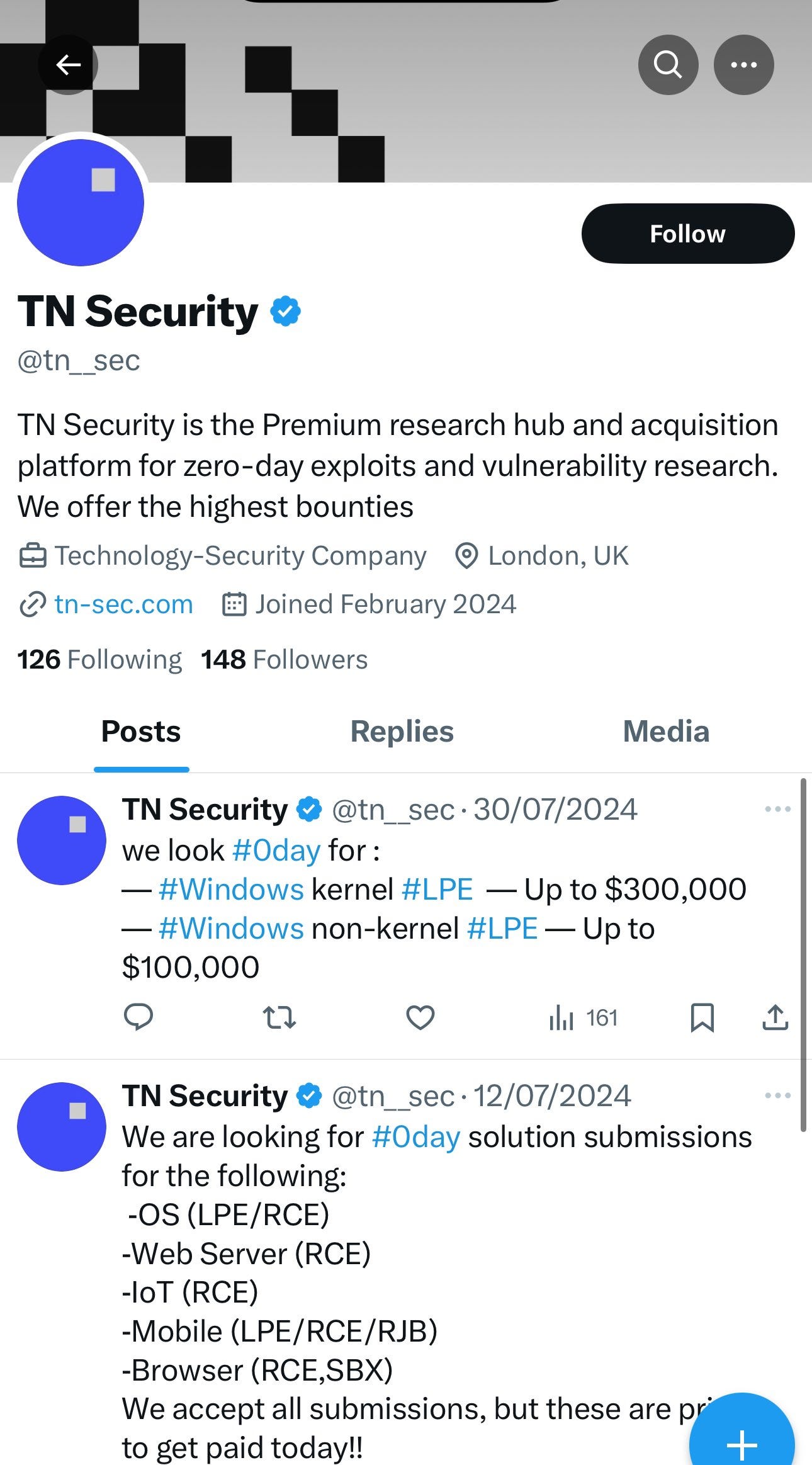
So they’re busy fishing for 0days, and are openly operating on Twitter and their domain:
They seem to be offering prices that seem to be to be a little low all things considered but I’m not knowledgeable about this.
The company is run by one girlboss named Anastasija Berezina, born in 2005. Career goals for sure.
This case also shows just how porous the UK Corporate registry is. Correctiv looked into Anastasija and this company, alongside otehr fronts, in the past in their past reporting here. Somehow, these companies are still active and plying their wares online.
The other point to keep in mind from this case is that IO is but one element of cyber activity, in particularly cybercrime. The diverse and profitable Russian cybercrime scene is critical in providing IO operators with the scale and capabilities that they need, and they’re certainly open to diversifying to 0days and other activity.
























You don’t get enough credit for your titles. This is brilliant!