Folie a Sudan
Welcome to Memetic Warfare.
The first thing that we’ll take a look at this week is a fascinating peek under the hood of Spamouflage infrastructure by my colleague Max Lesser of the FDD, as well as Sophie McDowall and Cat Smith, available here.
The report found over 25,000 inauthentic Facebook pages, suspected to be Spamouflage-related by virtue of sharing identical or similar names to previously identified Spamouflage accounts.
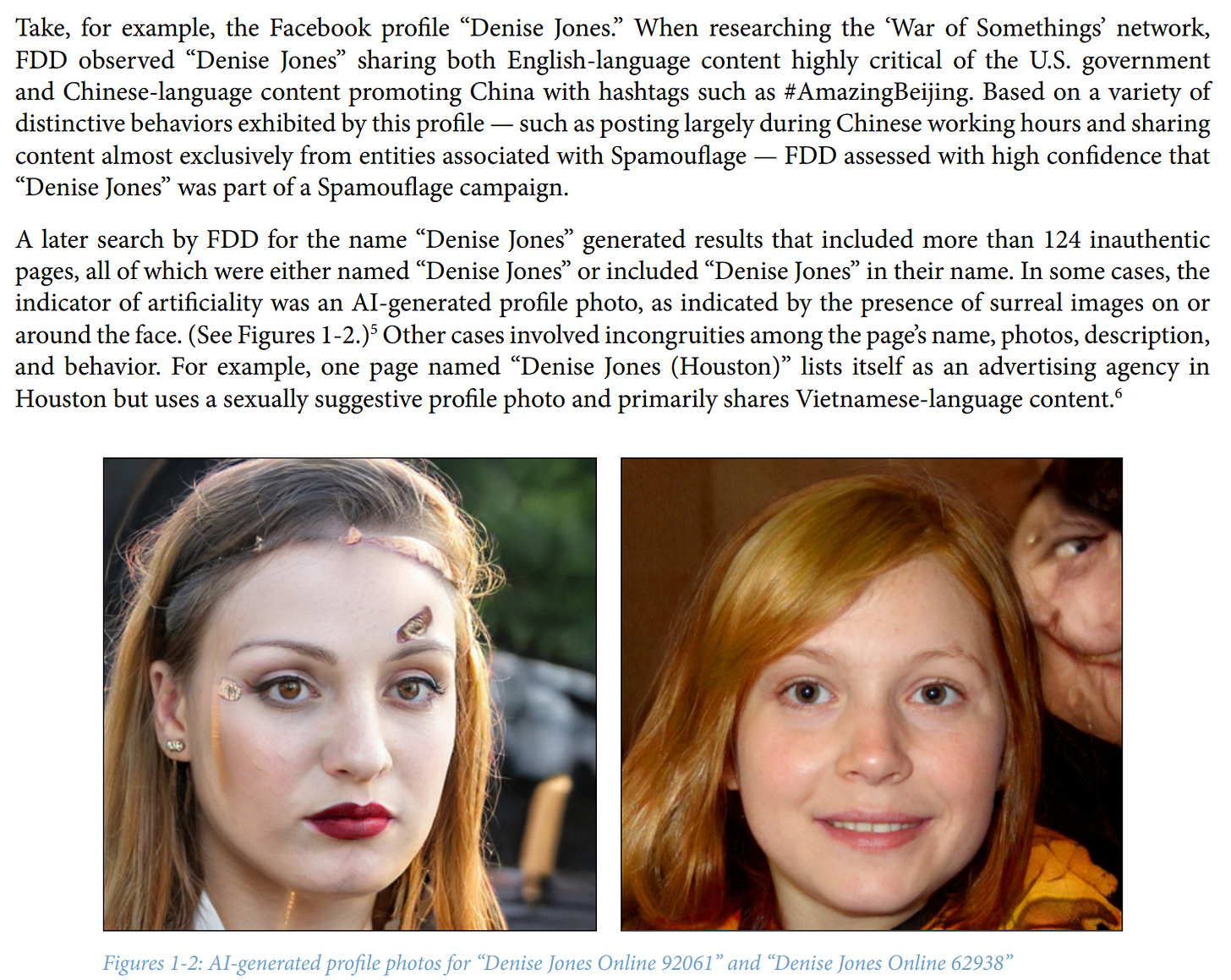
Take a look at the “Denise Jones” example below. Denise jOnes is an inauthentic account with over 124 entities with GAN-generated images or otherwise. At least one also posts in Vietnamese, potentially indicating the use of a Vietnamese content farm for outsourcing.
Searching for Denise Jones Online retrieves multiple other inauthentic pages:
There’s some evidence of Fewfeed, a black hat marketing tool, being used for automation:
The report also posits that alongside Fewfeed, Spamouflage may make use of purchased/hacked accounts - check out the results from Telemetryapp.io as well below:
The report is short so definitely read it, and it’s great to see a look at what actually powers Spamouflage and the scale that it operates at.
From here, we’ll move on to the Anonymous Sudan indictment, available here.
We’ve discussed Anonymous Sudan here in the past, and it’s one of the better-discussed hacktivist groups in the past year so if you want some background, just give them a google.
The indictment itself was surprising and shows the limitation that we often have in attribution. Many believed that they were a Russian hacktivist front group, and I was sympathetic to that claim. There are reasons for this, primarily:
The scale at which they operated, which was more impressive than many thought a small group, let alone two people, could pull off
Their cooperation with attributed Russian hacktivist groups and some overlap with Russian infrastructure
Posting originally in Russian
Their activity that often aligned with Russian interests and to a large degree not with Sudanese nationalism
The two Sudanese nationals, who also are brothers, were arrested abroad in an undisclosed location. These two ran an impressive operation with limited resources, and I think that there still may be some more information here that will come out soon that may change our understanding of their operation.
Not beyond the pale to think that these individuals worked, at least partially, at Russian direction. Getting more information about their arrest and whatever we’ll see in the trial will be illuminating.
The next point that we’ll bring up is the return of Volt Typhoon 3, with some tastefully-used Roman numerals below. The CVERC has been quiet for a while, so it’s nice to see that they’re still committing to the bit here. This report goes into “screed” territory, and continues to denigrate American companies, agencies and citizens while relying primarily on old leaked material.
Sentinel One has a solid review of the 60+ page report, available here. I’ll save you the long review of the report, but I’ll remind interested readers - like last time - that I’m working on a much longer paper on this specifically which I hope to get out sometime after the elections. For some good discussion of this, check out Security Conversations (a fantastic podcast that I recommend regardless) and their latest episode here.
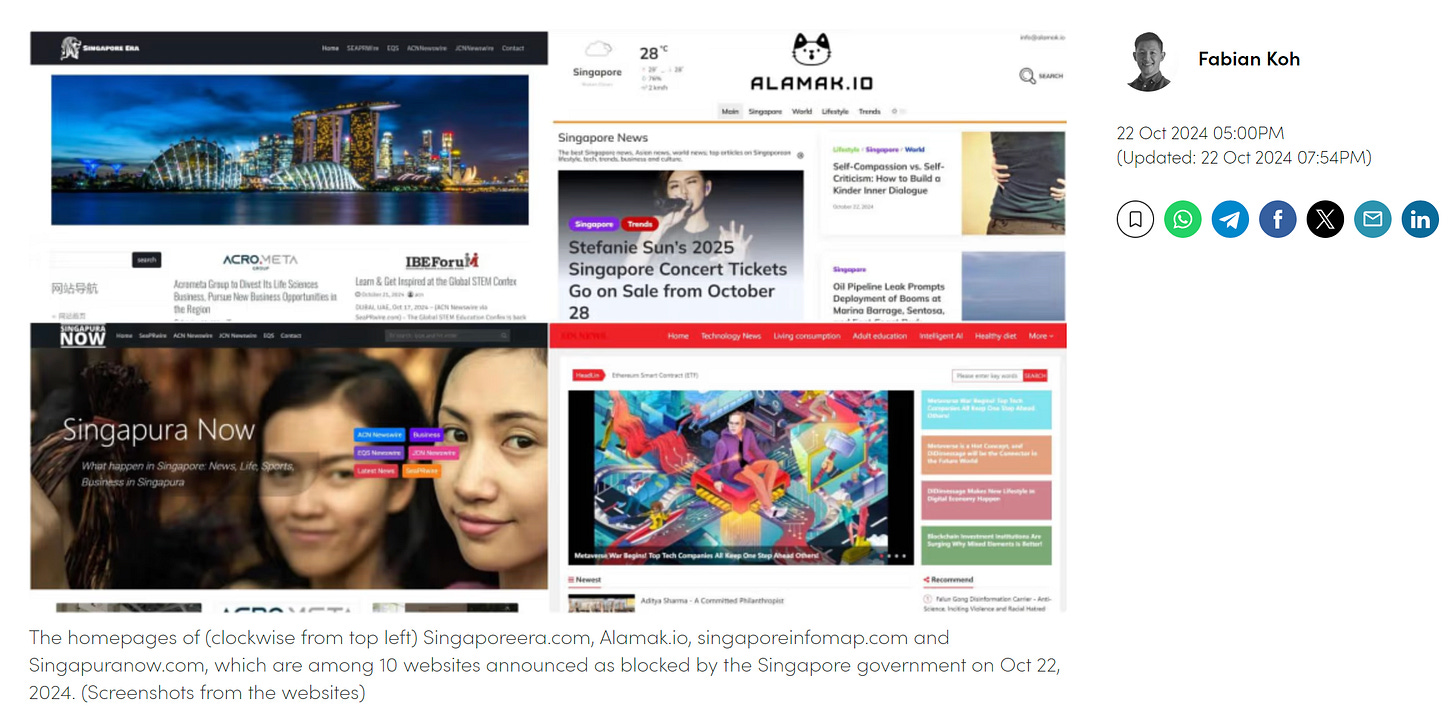
Let’s move on to another under-reported item in Singapore. The Singaporean Ministry of Home Affairs (MHA) has announced that they’ve blocked 10 domains “set up by foreign actors”.
Two of the ten domains are claimed to be part of foreign networks exposed by Mandiant and Citizen Lab:
Channel News Asia claims that these are tied to the Shanghai Haixun network:
These domains appear to be newly identified as part of the network, showing some quality investigative capabilities on part of the Singaporean government. As an aside, one of the things I always recommend is that people expand upon publications from TI providers to see if they can find anything new, which may be what happened here as well.
If most of these domains are tied to the network, then attribution to China is what makes the most sense, although the press release doesn’t explicitly attribute the operation.
One domain appears to be particularly interesting, Alamak[.]io. The domain is singled out as it has ties to Russia:
The claim about biological warfare research facilities to me screams Ukraine biolabs:
We can see at least one of the Russian ambassador’s articles on Alamak shared on Russian domain Pravda via AHREF Backlinks:
We can also see that someone has been busy with Wikipedia - checking out backlinks finds multiple links to Alamak on Wikipedia, primarily on the “Northern Sea Route”:
Let’s take a look at the domain.
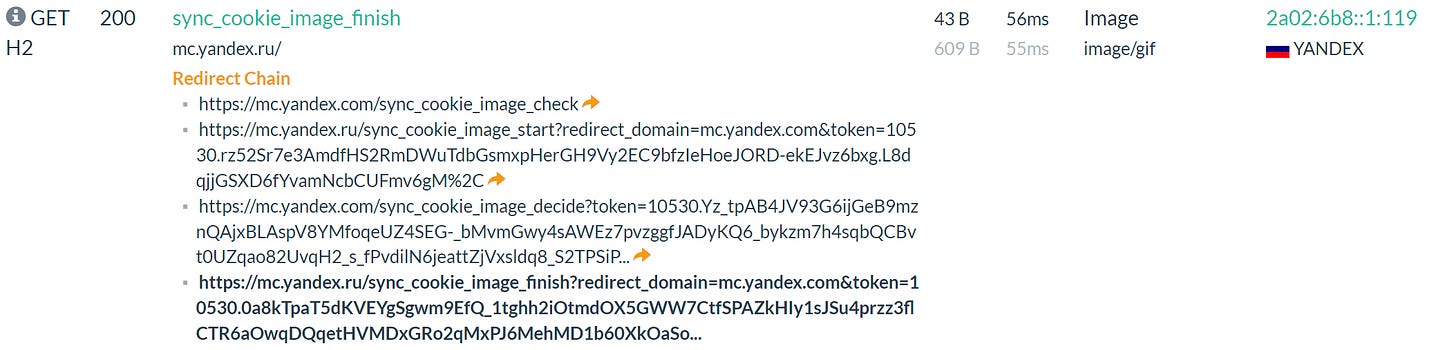
Checking it out on URLScan finds a Yandex Metrika analytics tag - already indicating that it may be Russian.
Looking at its previous host on VirusTotal, we can find Russian sites on the same host:
Moving to its current host, we can see that its PTR record shows that its a VPS:
Its current host is also self-signed and has multiple other Russian domains on it:
Censys shows different domains for its forward DNS requests:
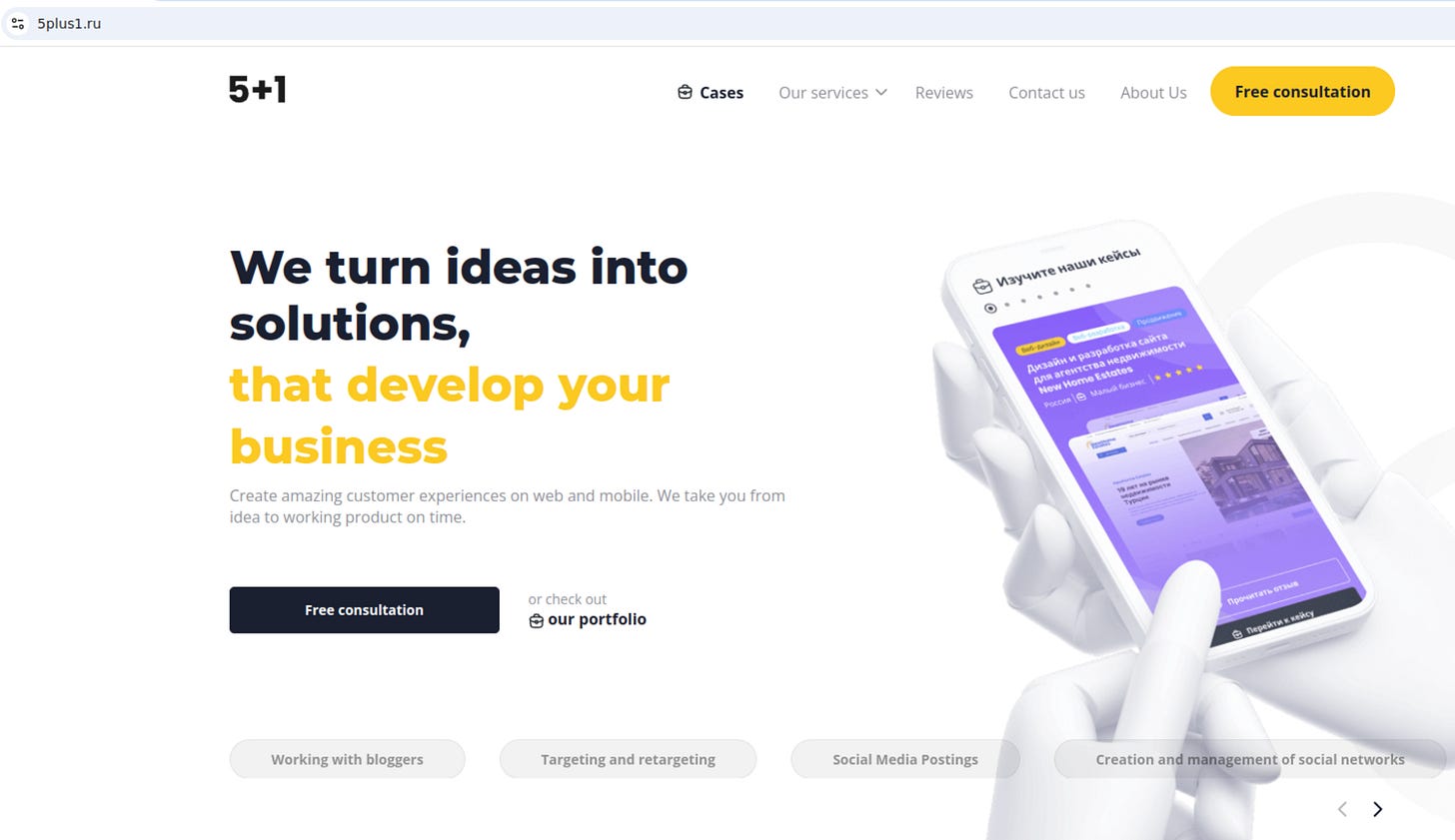
Let’s take a look at the 5plus1 domain. It appears to be a Russian (translated into English below) web and app development firm which also provides digital marketing services.
So the case here seems pretty cut and dry. However, the impact itself is notable - this is one of the first cases, at least of which I’m aware, of (suspected) Russian IO in Singapore. Keep an eye on Singapore going forward, as it seems that there’ll be more takedowns based on their past activity.
We’ll conclude with another podcast recommendation - check out the link for Thomas Rid’s appearance on Lawfare, specifically discussing the SDA leaks. Rid brings up some interesting perspectives, including one piece of data that may indicate that the leaks were in fact from an American agency (potentially).