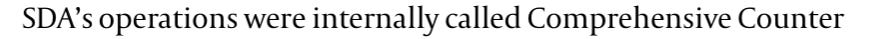doppelganger doppelganger doppel doppel doppelganger
Welcome to Memetic Warfare.
This week, we’ll start off with an administrative update, a recommendation for further reading, and then a long look at an even longer report on Doppelganger.
Just to let you all know, I’ve turned the historical paywall off for now. I may turn it back on again in the future, so no promises, but I want to try to keep as much of the blog as I can for free going forward and offer other things instead.
If you have any thoughts on this, just let me know. Some things that I’m considering doing:
Writing a specialized IO investigation-focused guide as an e-book
Holding public-registration, paid online sessions to review certain usecases
Perhaps looking into other forms of media as well
If any of those sound interesting to you, don’t hesitate to message me here or email me at ari@telemetryapp.io.
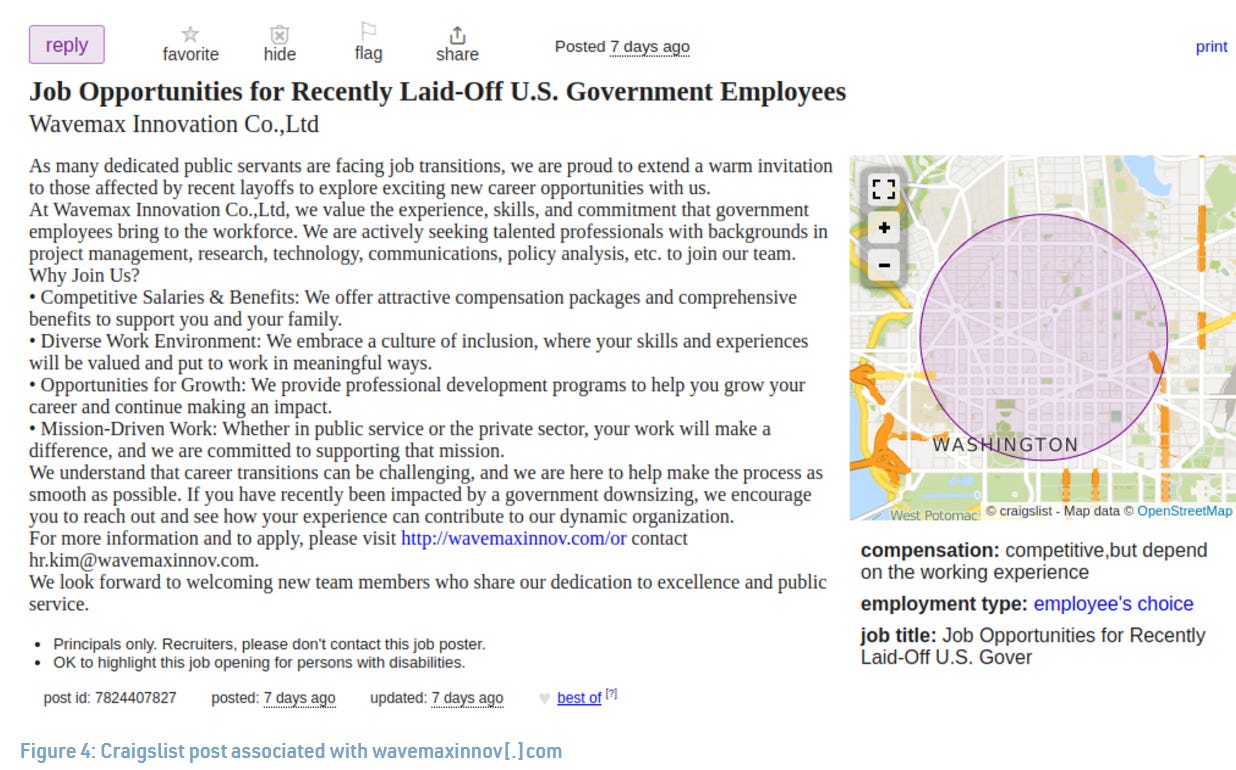
So, let’s begin. The first topic of this week is a recommendation from my colleague and friend of the blog Max Lesser. Max published a fascinating investigation report on an apparently Chinese network of recruitment domains. The report has a bit of everything - a lot of domain analysis and practical techniques and even Craigslist.
This is especially interesting as a topic, in my opinion, on the backdrop of the DPRK IT workers. Comparing Chinese and North Korean efforts shows that the DPRK, interestingly enough, seems to do a better job of creating original, unique domains and penetrating targets, though it’s unclear what success, if any, the Chinese had.
We’ll then take a fika and review The Swedish Psychological Defense Agency’s look at the SDA leaks:
This is one of the lengthier reports I’ve seen on IO, so we’ll focus exclusively on highlights. Regardless of my thoughts on the report (which are mostly positive), it’s great to see some truly long-form research being done as the space matures. Check out the structure below if you want to skip to a certain part of the report:
Their executive summary is available here:
So, here’s where it starts to get more interesting. The report’s main claim is that DG itself is not actually that interesting or effective, and that it’s main power is being exposed:
These are points that many people have made in the past, and while I agree, I wouldn’t present them as being overly new. The next framing point is a bit more interesting, and one that I agree with also beyond Russia: understanding cyber/IO ecosystems and private-sector capabilities/actors is the next big step that is currently ongoing in the industry.
The rest of the intro is a bit long, but I do appreciate that they call out companies that they disagree with:
We’ll keep moving also. It gets a bit more interesting when the authors posit that SDA leaked the data themselves, while I personally have always thought that it was a Western state.
The report dives into the people and structure behind the SDA and its affiliated companies which is good, the only thing I want is the leaks themselves to be released:
After a lengthy and detailed section about SDA and various satellite organizations, we get to the section discussing how this framework actually operates. I liked the choice of usecases that show the nature of decisionmaking:
There’s more after this as to how SDA works, the bot networks and so on, but it’s too detailed to cover here, so we’ll move on to one of the more interesting sections: exposure. The report discusses the “crossroads” that Doppelganger faced after its exposure: either being shut down or further invested in due to the volume of coverage. The SDA itself got involved in amplifying its impact - a critical dynamic often underdiscussed. Threat actors of all kinds have to justify their existence to their funders and thus try to make numbers go brr, promoting quantity over quality and incentivizing poor operational security.
The leaks further emphasize this with the SDA being tasked itself to “create a register of the mentions” of their operations.
This is made clear in the text of the requested report:
This becomes especially clear with the next step taken by the SDA in October 2023 - the “FGIA (France-Germany-Israel-America) Project” and its accompanying report on its impact:
Exposure of Doppelganger itself is a key tenet in the five points made in the document:
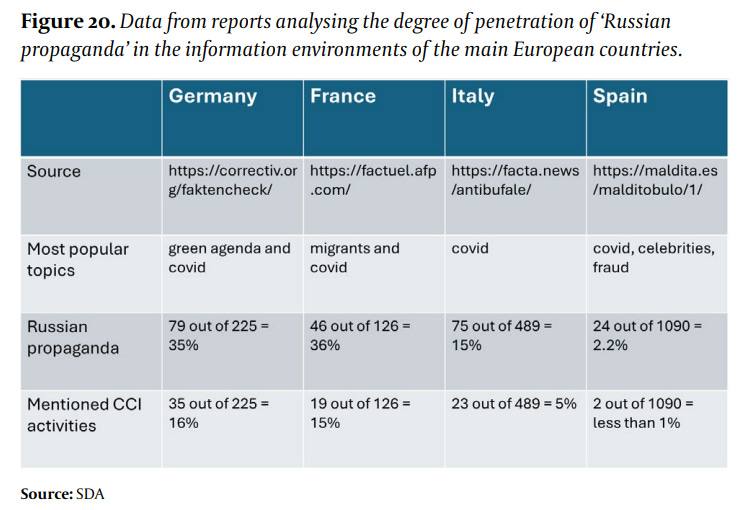
The report shows that the SDA took data on factchecking and coverage of their and other operations in target countries:
The report posits two main findings on the exposure of Doppelganger: Firstly that it provides a sense of proportion, showing how significant DG/adjacent operations are in France, Germany and Italy:
Secondly, that, the SDA/Russia view this type of activity not as regular “PR” or advertising work, but rather as a type of warfare - showing that any “penetration of enemy territory” with their content, data and narratives is good:
As per the leaked documents,the exposure of DG apparently led to it receiving more funding and growing significantly and changing workflows and structures:
We get a nice screenshot showing the new workflows used by the team and how they operate - I especially find the use of manual monitoring of 70 ish Telegram channels in contrast to automated social media monitoring to be an interesting point. We also get a screenshot showing how the SDA plans its campaigns and uses online platforms - Viber being a call center is an interesting choice.
The newly restructured organization carried out a few campaigns targeting the EU elections, Ukraine, Israel and so on, and then used statements from EU officials to show its own impact:
Fact checkers are also cited:
One of the more interesting sections for me covered tooling. The report provides screenshots of samples of reports generated by a comment bot management platform:
We also get a look at the call center that used Viber to carry out over 1.6 million calls apparently:
Messaging applications get a shoutout, with Signal being a leading platform, which is a datapoint that I found fascinating, I’d love to learn more about exploitation of Signal.
The report looks at leaked content indicating that the SDA was interested in the CIS region:
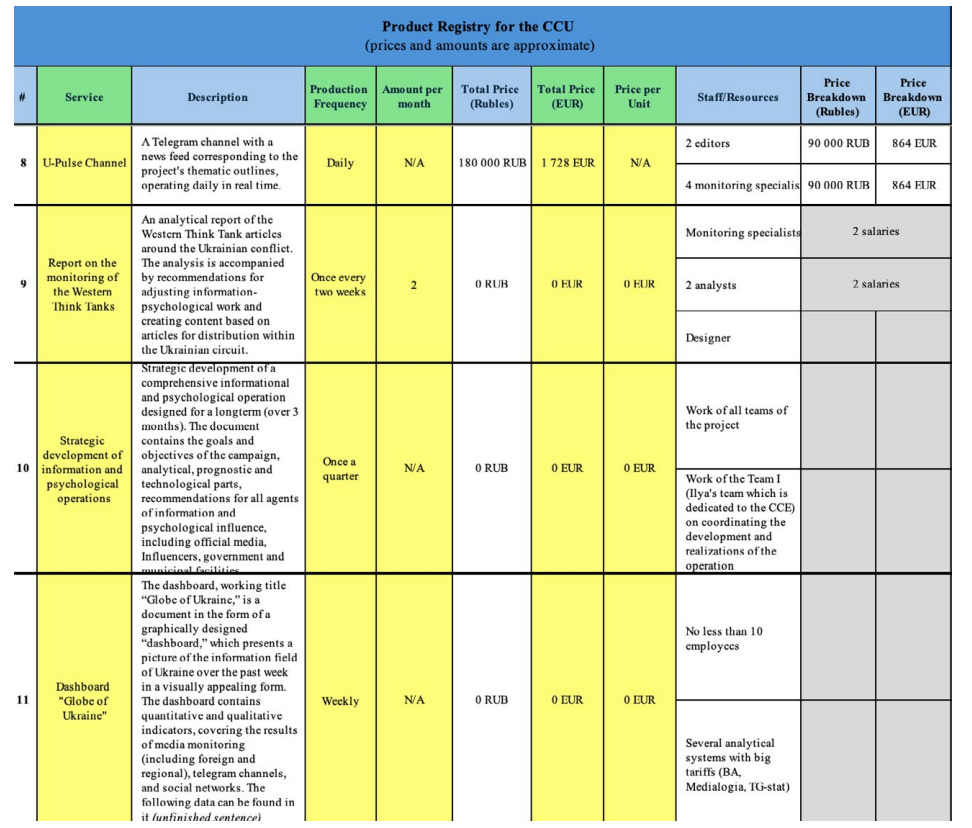
The last chapter of the report covers SDA’s capabilities, deeming them to be 5-7 years behind the curve or so, though it’s not clear what the avant garde equivalent would be. I was drawn immediately to a list of the products and services purchased as well as a general budget for manpower:
Some truly excellent things here, and it’s great to see even more of the primary data from the leaks actually published. Imagine being the papmphleteer or poet on the SDA staff, or alternatively the person who has to monitor Western think tanks.
The report then dives into specifics, such as international media monitoring:
Narrative monitoring:
Other topics, like influencer management, public opinion surveys, comment analysis and the highly-scientific sensitivity index:
The final section focuses on analytics. We have a review of previously exposed dashboards and a review of capabilities from posting to meme creation.
We’ll skip ahead then to a more interesting section, “Guerilla Actions”. The section looks at petitions and protests promoted by the SDA to some degree of success:
The report then reaches its conclusions and recommendations. The first recommendation is to begin considering threat actor capabilities as capabilities and not as TTPs. I’m in favor, as IMO anything that gets us off of the TTP-centric framework is good and may be more effective.
I also liked the take on countering IO, and FIMI still sounds ridiculous.
There are a few other recommendations - targeting finances, improving coordination and other typical European memes that are required in these sort of reports. These are all well and good, but don’t really mitigate or disrupt this activity effectively, as it simply cannot be mitigated completely, at least in ethical/legal ways in democracies.
That’s not to say that nothing should be done, but that the response isn’t a defensive whole of society response necessarily, but rather something more targeted and proactive from certain law enforcement agencies.
This was a long one, so we’ll conclude here. The industry has been in a slowdown as of late, and I’m not sure that we’ll see frequent publishing from previous industry standards, hopefully that changes soon. In the meantime, it’s great to see other government/government adjacent organizations stepping up and publishing long-form, deep research.