Don't Cyber-attribute As This
Welcome to Memetic Warfare.
This week we’re back to the evergreen topic of Chinese cyber attribution with two big developments. We’ll first take look at the Chinese attribution of alleged Taiwanese cyber and IO operators and then at China’s attribution of an alleged US cyber operation.
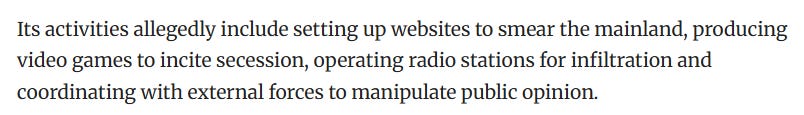
Let’s kick things off with Taiwan. As covered in Chinese media outlets, the Fujian bureau of the MPS exposed 18 members of a Taiwanese “psychological warfare” military unit.
The attribution included their names, photographs and ID numbers, and even offered a meager bounty of 1,400 USD for their arrest.
This attribution follows on the heels of recent Chinese attributions of allaeged Taiwanese cyber and IO activity - see the latest Memetic Warfare post on it below:
The attribution accused these operators of a range of activity , including “broadcast” operations such as radio stations, “coordinating with external forces” (unclear who), and most interestingly - “producing video games to incite secession”.
This attribution is interesting for a few reasons. Firstly, it comes from the Fujian MPS, which is the closest province to Taiwan, thus it makes sense that they’d be focusing on this. Secondly, in contrast to attributions of US activity, this attribution (and other attributions of Taiwanese activity) include pictures, names and detail.
Chinese attributions of Taiwanese operators are thus more plausible, both by virtue of their detail, Chinese proximity both geographically, linguistically and culturally, and Chinese investment in espionage against Taiwan. While this one may also be politically motivated and a diversion from Chinese activity, it probably has more of a basis in reality than Chinese attributions of other activity.
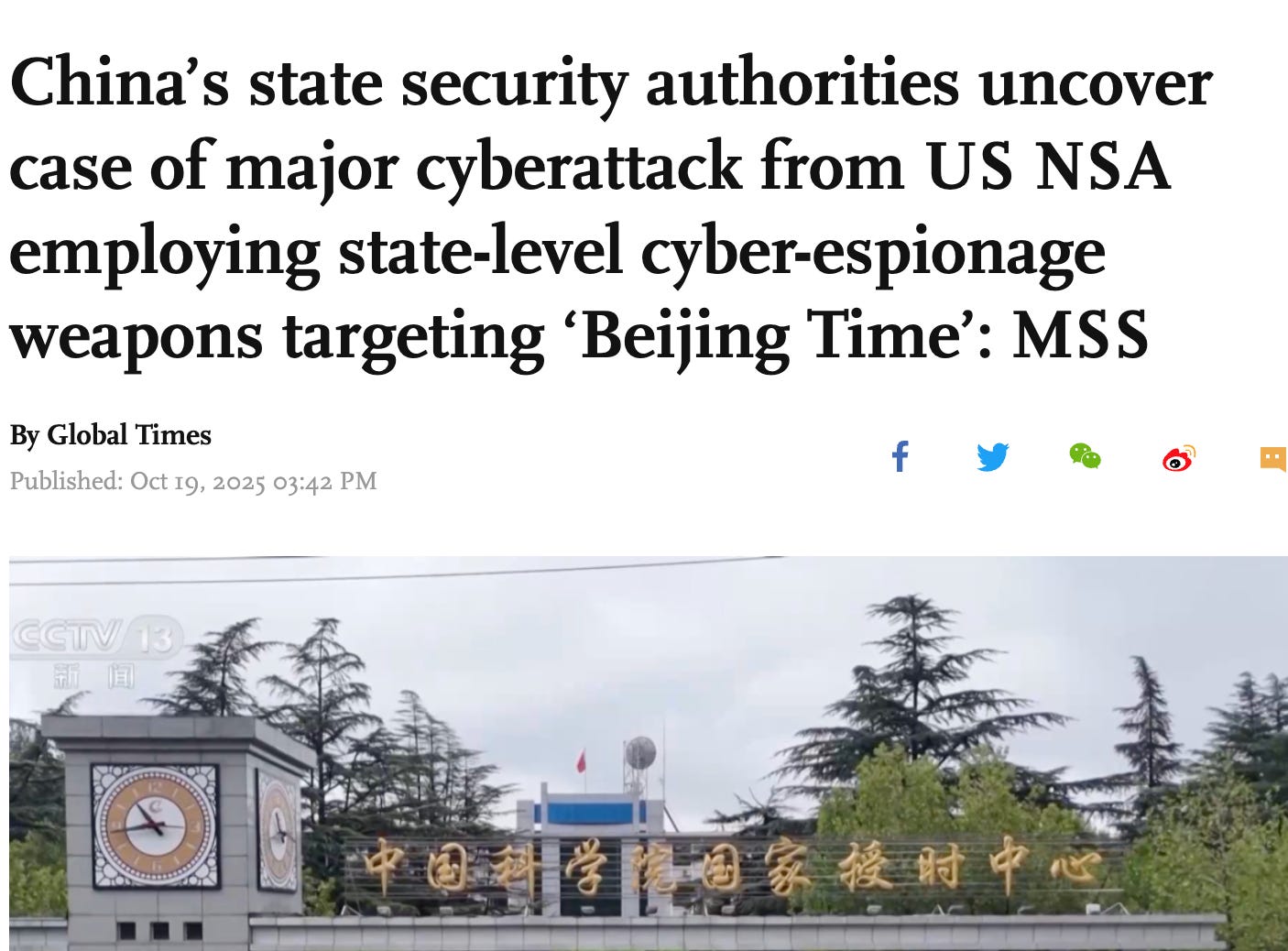
Contrast that attribution with the Chinese claim that made headlines recently, the Chinese attribution of alleged US operations targeting the Chinese national time center covered, as usual, by the Global Times:
The article claims that Chinese authorities have uncovered an NSA intrusion into the center, claiming that the center targeted “generates, maintains and broadcasts “Beijing Time”, providing precision time metrics for other services:
The article claims that the purpose of htis would be to cause network failures, mess with transportation and more.
Smarter people than myself have posited other reaosns reasons as to why the US could theoretically want to do this:
Controlling time could be useful as part of further cyber espionage (could make dead certs useful again, could make other certificates expire, target other services and so on)
Could be useful to target GPS services - making the time different with satellites e.g could throw off navigation
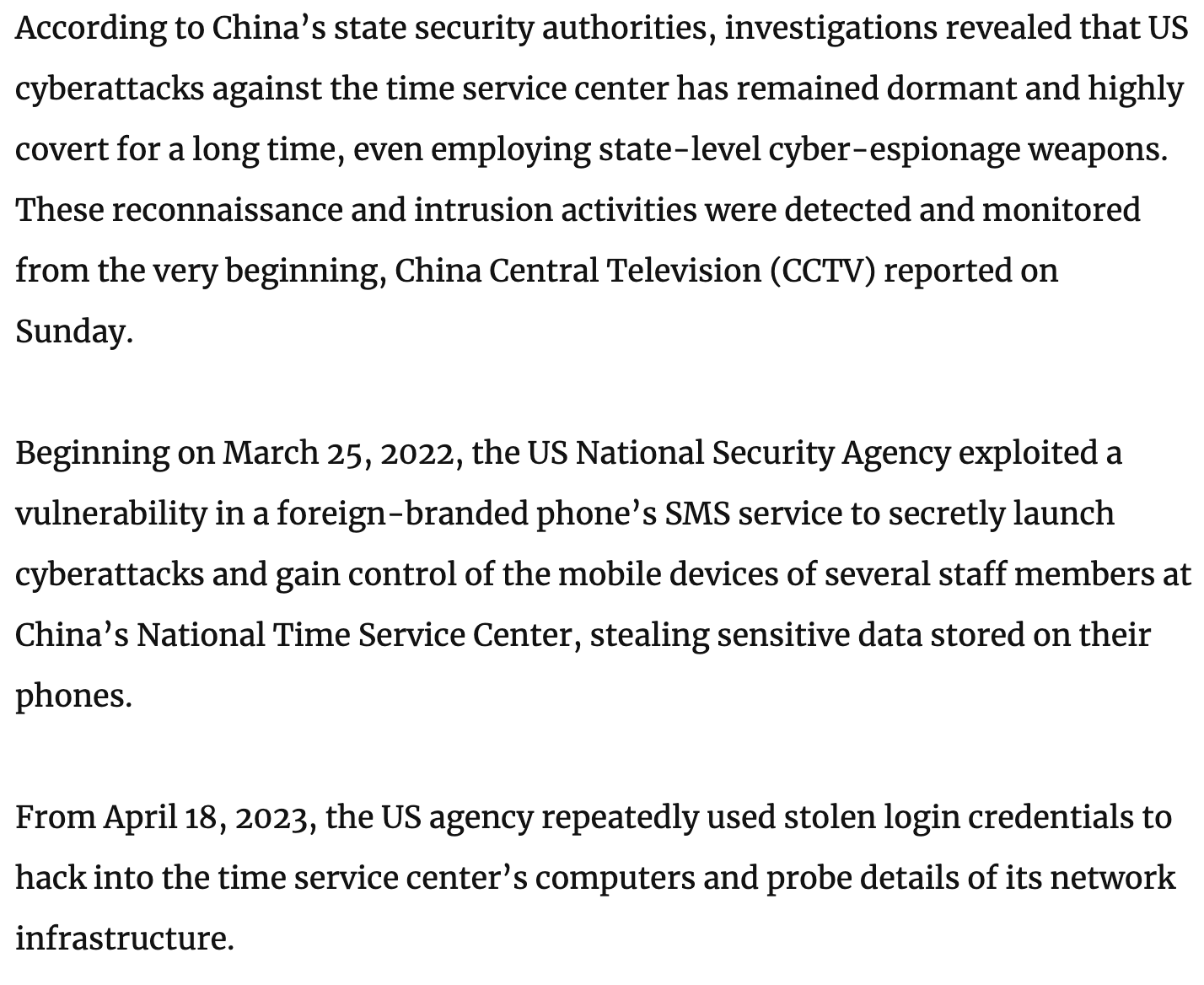
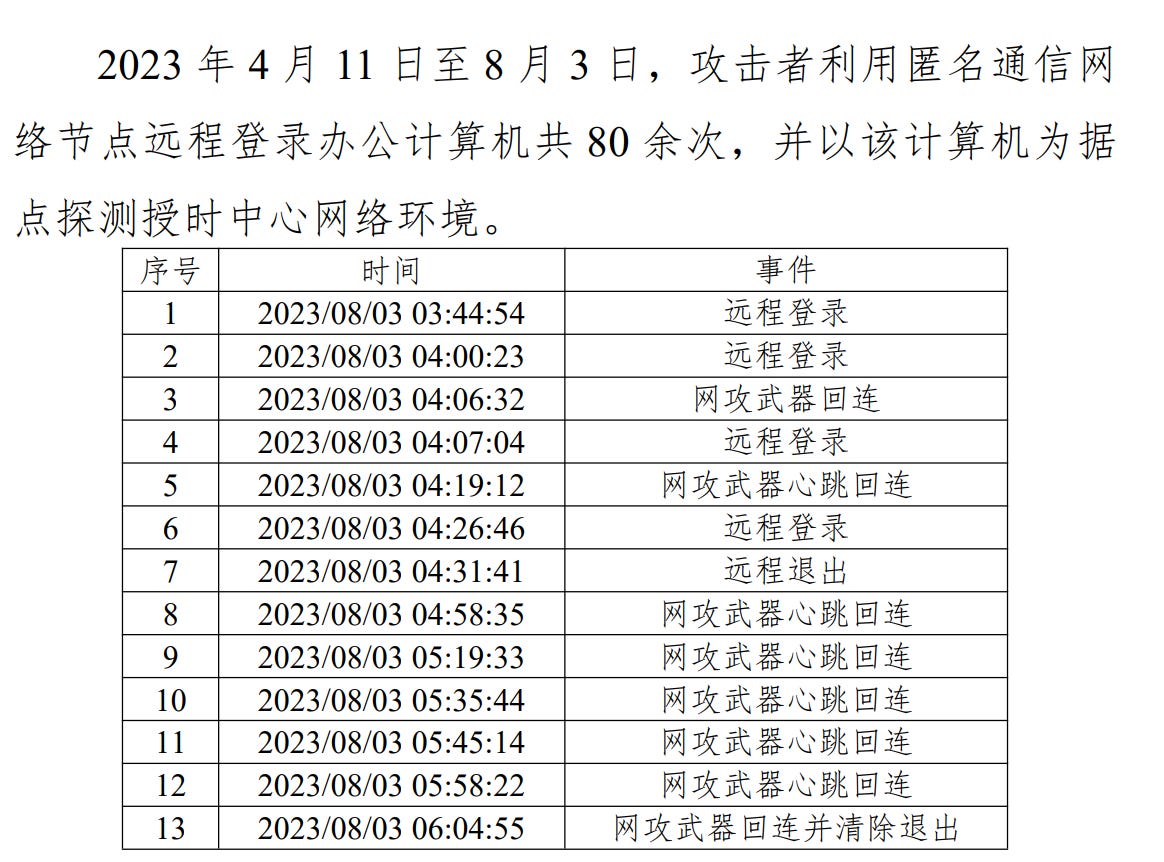
The article provides some other detail, stating that the operation was “detected and monitored from the very beginning”, having begun in 2022 with an attack against a “foreign-branded phone’s SMS service”. The phrasing here is a bit odd and seems like it points to a proprietary SMS services of a specific foreign phone brand, sounding like Apple iMessage.
We also get some meaningless sections about the use of VPSes and “encryption algorithms” to hide traces:
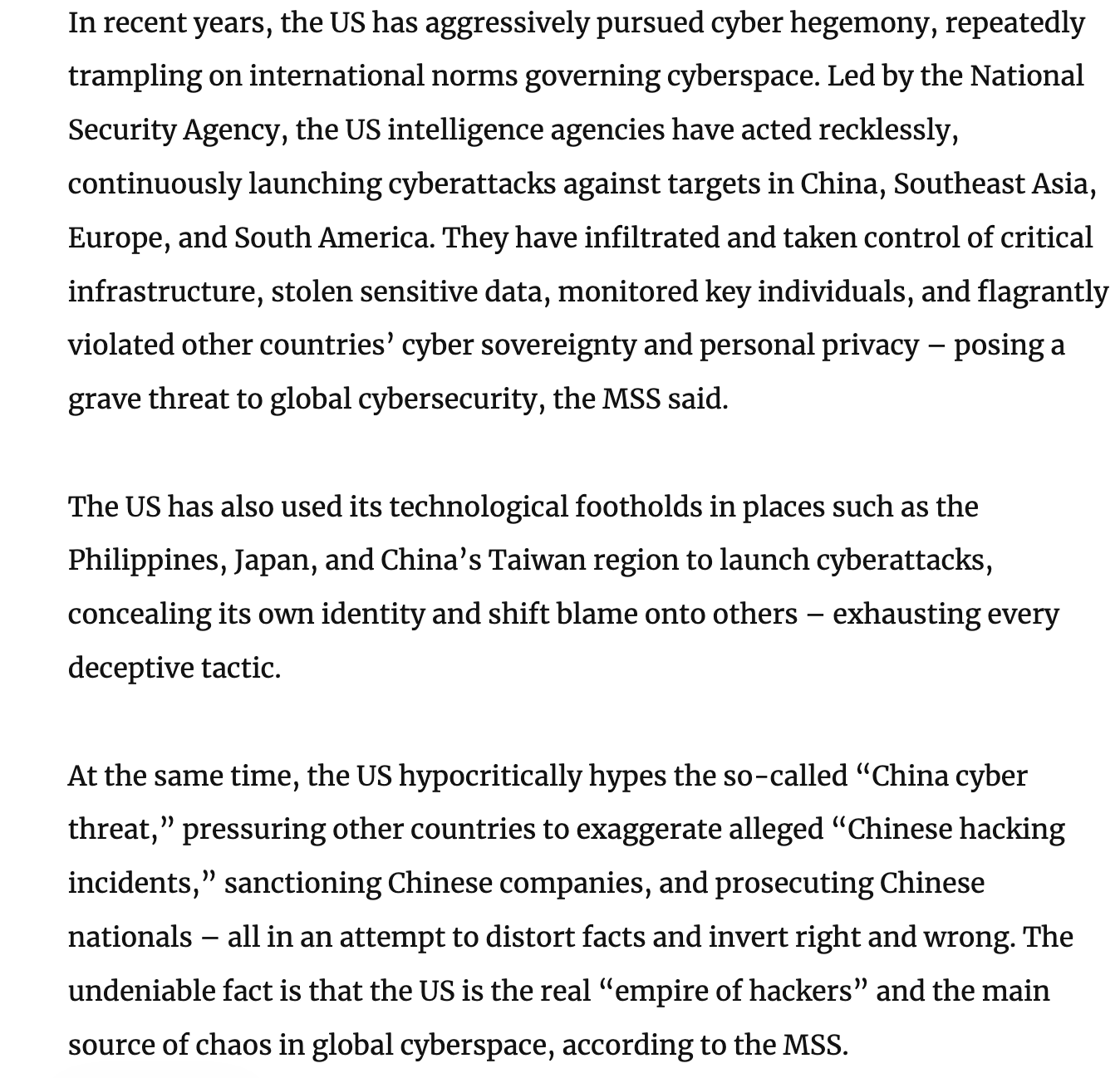
One of the recent trends we see here also is China not only playing the victim, but rather playing up its own capabilities to a foreign and domestic audience:
And of course we get the propaganda/IO section towards the end, blaming the US for acting “recklessly” and using recurring phrases like empire of hacking and “China Threat”.
As we also see occasionally with the Global Times, an op-ed also published in the Global Times also says the quiet part out loud:
Here, after the requisite section slamming the US, we see the real point being made here: China is more capable in the cyber-realm and can “defeat” foreign cyberattacks:
China apparently will use this also as a way to build bridges with other countries allegedly suffering from US malfeasance:
Presenting China as a capable defender in the face of alleged US operations makes China look good both domestically and to foreign audiences, and it seems that China will try to maximize the impact of this internationally.
Interestingly, this claim also made headlines across Western outlets, who mostly covered it uncritically as a news item, including Reuters, Fox News and others.
While it’s certainly possible that the US actually did this, IMO it’s irresponsible for Western outlets to cover this as a regular news item without caveats, especially considering that most of them didn’t review any technical writeups.
The same thing happened with the latest Chinese attribution of alleged NSA operatives, which I personally think was entirely made up. This case may not be, but there isn’t enough here to assume.
There is in fact a technical writeup in Chinese from the CNCERT, available (archived) here.
This report is much more detailed than the average CVERC or other report we get, including information such as login logs:
Use of implants named “back_eleven”, “eHome_0cx” and New DSZ Implant:
We then have multiple pages of reverse engineering which we can’t confirm is accurate, and a table of IP ranges as indicators, which in typical fashion is useless as is.
While higher-quality than other Chinese reports and providing more detail, as per usual we don’t see useful indicators of compromises, full hashes or other information that could be used to recreate the findings or threat hunt.
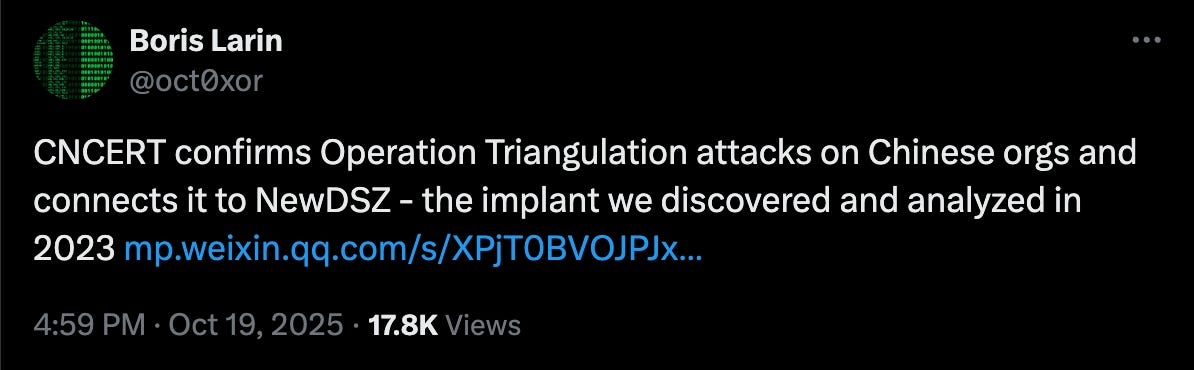
What is interesting is that the report specifically referred to NewDSZ, the malware used in operation Triangulation, as mentioned by Kaspersky research:
It’s unclear if this in fact actually used the same malware. The report mentions how advanced the NSA is but also then claims that they used the same malware and techniques this time which is how they were so easily caught? Bit odd, but the reference here is interesting regardless.
If it’s really the same malware, that is interesting and we can begin to see patterns in how the NSA operates, a possibility that I believe is low.
The other, more probable option IMO is that the report here is trying to build on the reporting on Triangulation to appear more legitimate. Wouldn’t be the first time that Chinese actors refer to Russian activity!
The final thing I’d add to this story is that, similar to the past (IMO fake) attribution of NSA operators, this story also enjoyed significant news coverage in Western media. That’s not to say that China wasn’t actually popped here - the target may well have been - but this stuff shouldn’t be taken as face value, and whoever makes the decisions about this may decide that cyber attribution is a solid route with minimal fact-checking.
That’s it for this week, thanks for reading.