Conjunction of the Slavs
Welcome to Memetic Warfare.
This week we’ll catch up regarding Moldova. For those of you who aren’t aware, and it’s fine not to be, Moldova’s upcoming parliamentary elections are a huge target for Russian interference. Russia tried to swing the past referendum and almost arguably did, so this is their next chance at turning Moldova away from the EU. Check out Memetic Warfare’s last look at Moldova here.
On that note, we’ve seen tons of activity from Russia, which Recorded Future covered very comprehensively, available here. Their report goes ongoing operation by operation, showing how almost every ongoing Russian influence operation has shifted its focus or at least begun to target Moldova.
I’ll share the key findings below:
Most of the research here recaps and covers past reports from RF and other outlets, but it does bring up a few new developments, such as an alleged forgery, the MD24 network and some other fun stuff.
The most important thing to note here IMO is the strategic element of how these operations act differently.
There are multiple Russian and pro-Russian outlets acting here - from the Evrazia movement to the SDA and R-FBI and beyond, and seeing how each one plays its own role shows how effective and holistic strategic targeting can be. That isn’t to say, though, that most of this is necessarily fully operationally coordinated at the highest level.
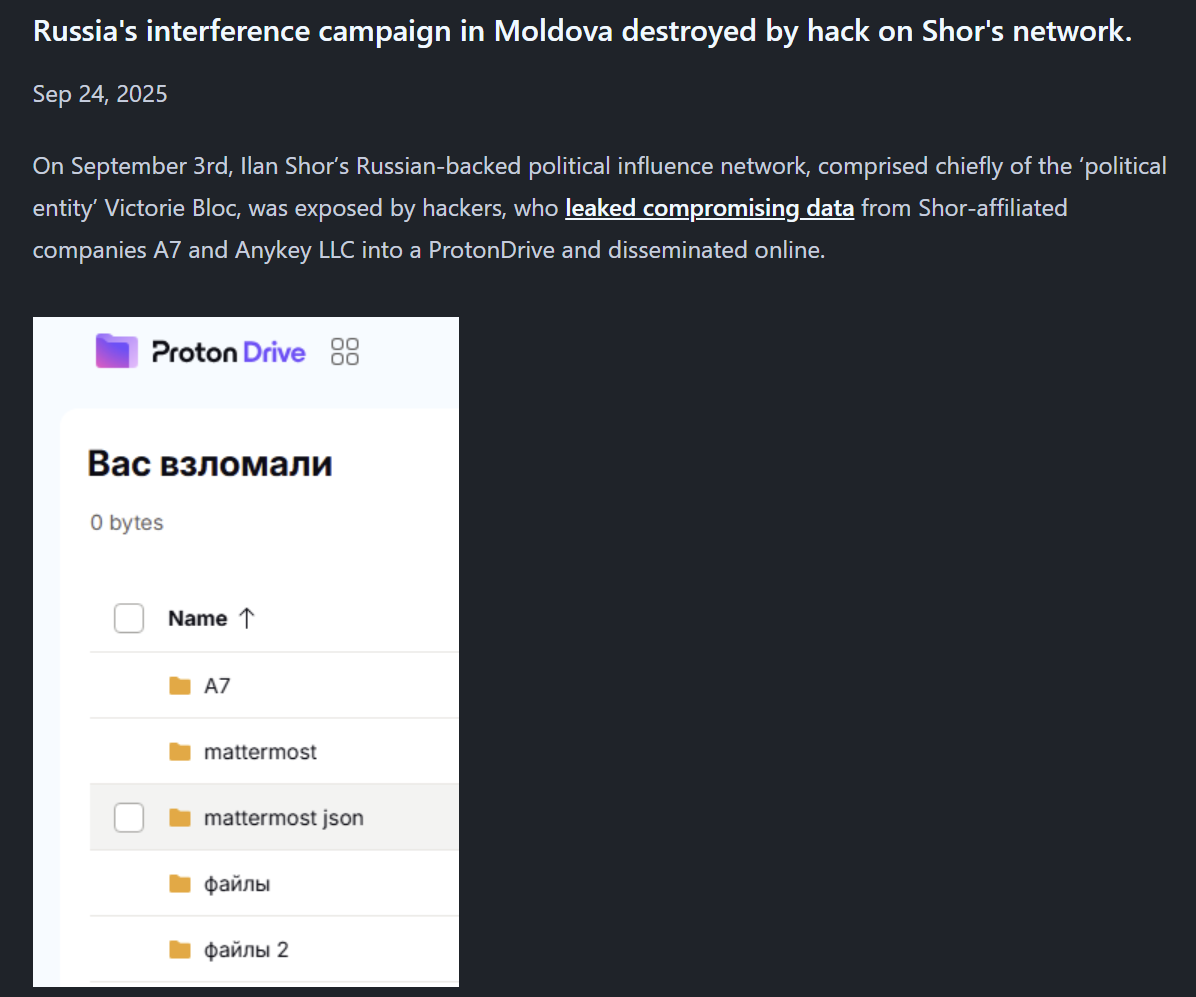
The next interesting development regarding Moldova is a hack and leak campaign targeting Ilan Shor’s Evrazia network, written up here on the “Where is Russia Today” Substack.
The hack and leak, as usual it seems, took the form of multiple files uploaded anonymously to a file sharing service, in this case Proton drive. Reminds me of the i-Soon leak on Github and others, though this is a pretty common style of disseminating hacked content.
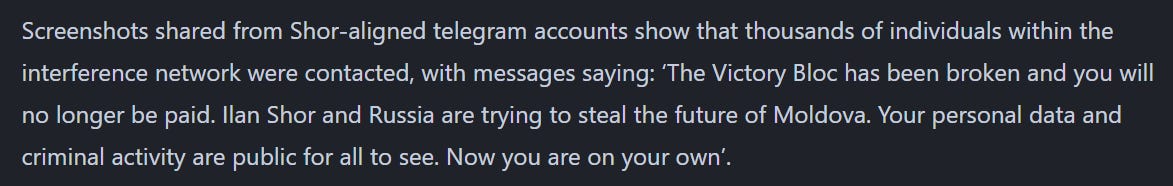
There’s a lot of data, including lists of individuals paid to protest, vote and so on:
These people were also targeted with messages, telling them that they will “no longer be paid” and that their data is “public for all to see”:
Certainly an interesting operation. Could be a hacktivist group of angry Moldovans, Ukrainians or whoever else that targeted two front companies used by the network (stated in the article), or could be a nation-state operation from any Western state that wanted to prevent Russia from operating in Moldova. Regardless, nice to see an actual preventative or proactive counter-IO operation utilize cyber and IO to target operators.
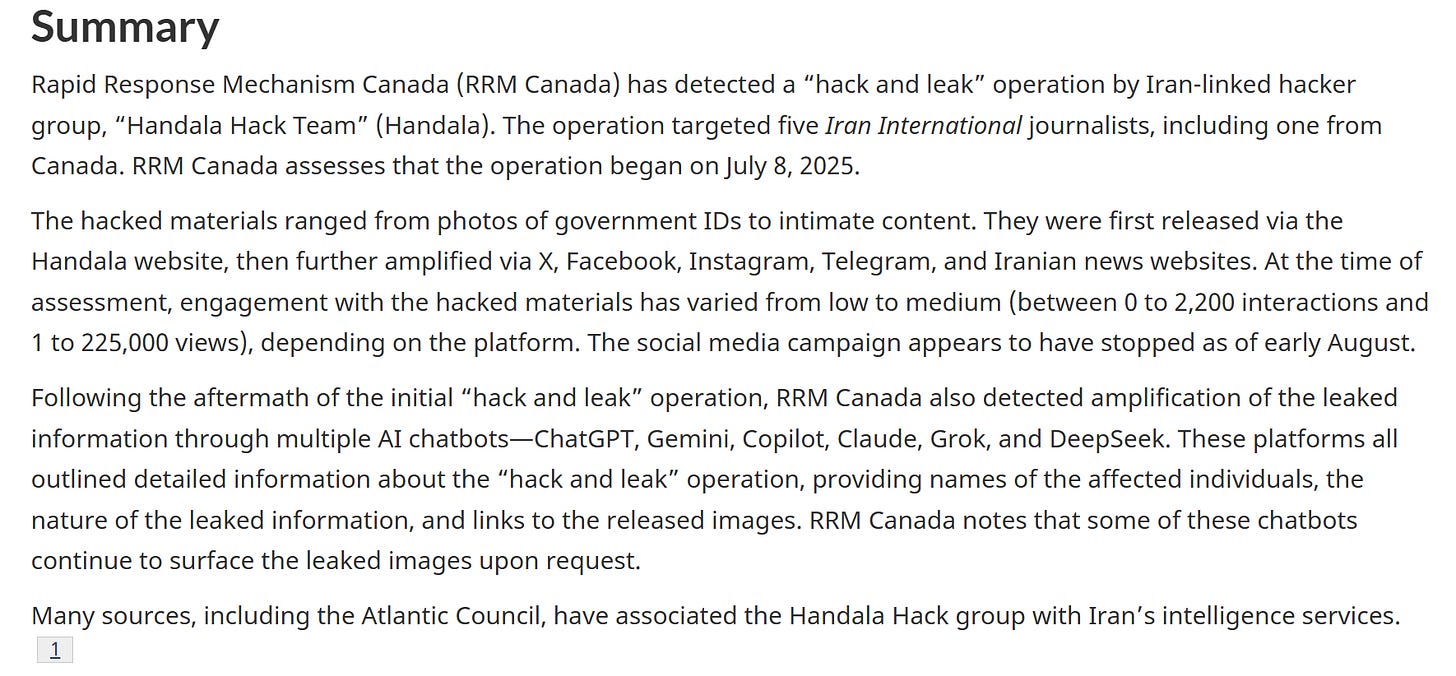
We’ll conclude this week with an alert from Canada’s Rapid Response Mechanism, which apparently is a thing, regarding the recent alleged compromises of Iran International journalists by by Handala:
While nice to see in of itself, the actually interesting part is that they took a look at how these leaks impacted LLMs, showing that many of them ingested them and share information.
That’s it for this week then, thanks for reading.