But why malicious models?
Welcome to Memetic Warfare.
This week we’ll look at a few shorter topics.
We’ll start off with a Unit 42 report on an Iranian phishing operation, available here.
The report examines an inauthentic website impersonating a legitimate modeling agency based in Hamburg:
The seemingly-legitimate site then runs an obfuscated script when visitors access it, which does the following:
This was interesting to me as it showcases a few things that in my opinion are very relevant for those that investigate IO.
The first point is that domains used in operations themselves can be collect a ton of information on users beyond just their natted (if unfamiliar, google NAT) public IP. The site operators can also fingerprint visitors in multiple ways - HTML canvas fingerprinting, enumerating their languages and plugins, resolution and more.
This may not be news to many readers that do domain analysis or enjoy operational security , and I certainly hope that it isn’t, but this enables those that operate domains to not only attempt to track individual visitors, but also to gather metadata as to types of visitors visiting their site beyond location for campaign metrics.
Going forward, IO sites could potentially provide targeted content on a site for users, especially when done automatically by LLMs
From an investigative standpoint, the report also does a great job showing how we can find and look at API endpoints on sites to better investigate them, something I’ve only seen done a handful of times in IO investigation.
The next topic is cyber attribution.
I know that I talk a lot about cyber attribution in regards to Chinese, Russia, Iranian and other activity and only occasionally mention Western activity.
The fact that Western operations even come up on this blog is something rare in the industry as of late, something that a recent paper covering attribution of Western cyber operations shows.
Abstract below:
I don’t want to go much more in-depth as it’s a bit long and academic, which is fine, but one graph tells the story well - there wasn’t a ton of reporting on Western cyber operations in the past, but the little there was is now greatly diminished, for a few reasons:
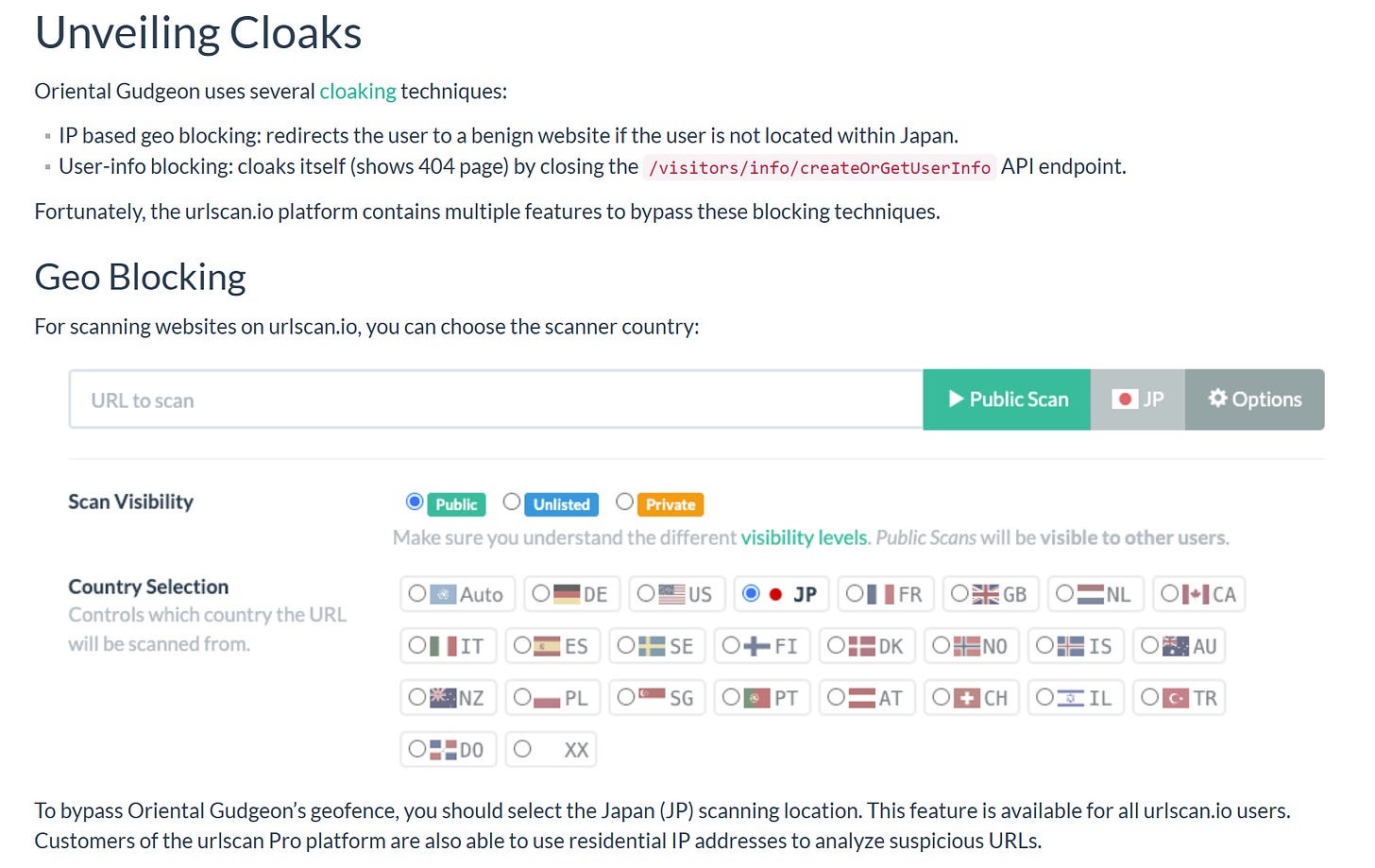
Next, I’d like to give a huge shoutout to URLScan’s first published research, available here.
I am an unabashed fan of URLScan, so seeing them set up a research team is fantastic, and we get some advanced tips:
I’ll be following them for sure going forward and dream one day of getting Pro access.
Last, shout out to NetAskari, a new substack focusing on China/Cyber/IO/whatever else comes to mind. See one of their recent posts below:
That’s it for this week. As always, check out Telemetryapp.io and see you next week.