Agentic maneuvers in the dark
Welcome to Memetic Warfare.
This week we’ll take a look at some older content and start with Microsoft’s 2025 Digital Defense report, available here.
It’s a long one, so let’s start with the table of contents for anyone who wants to dive in:
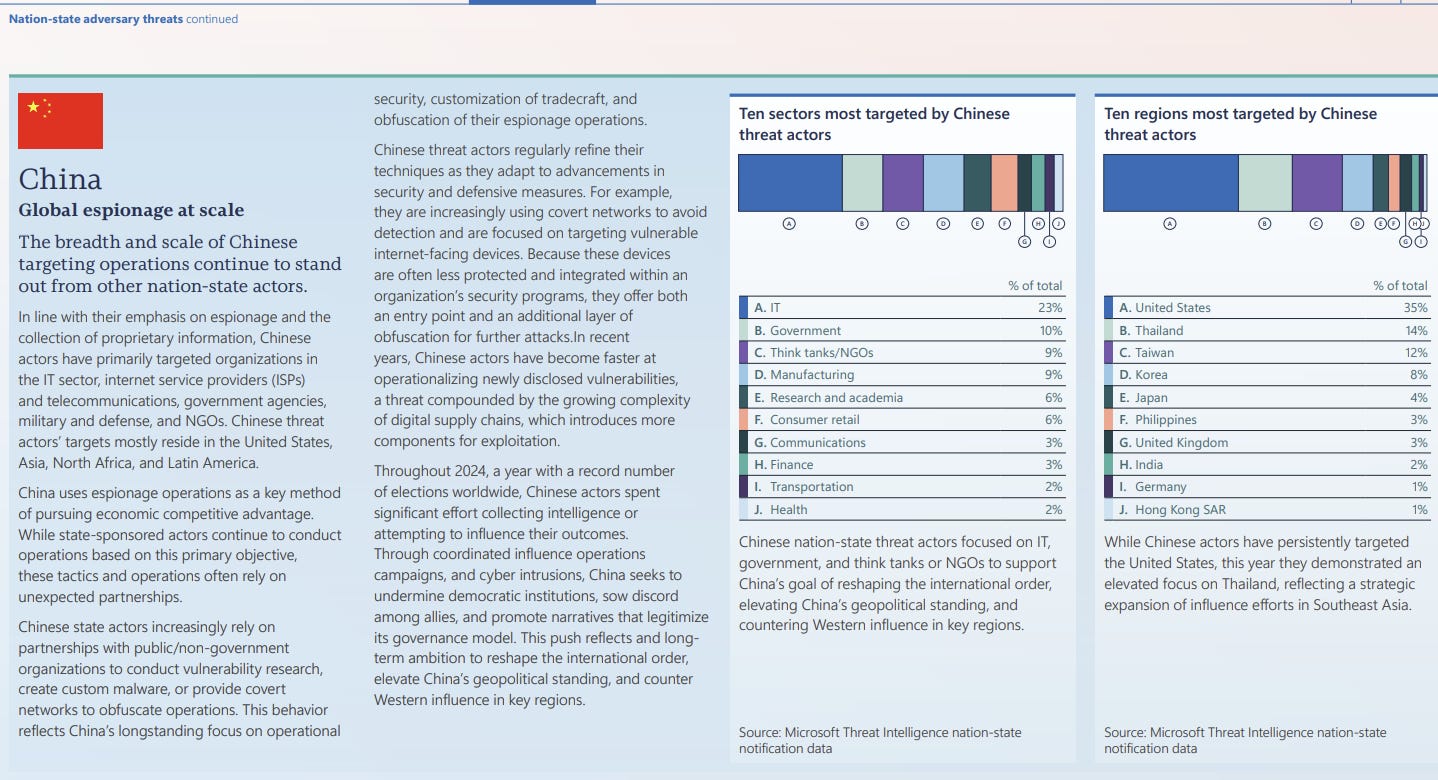
Let’s skip right to China. Shocking news: China is very active. The interesting section here re IO is short, referring to Chinese actors investing “significant effort” in collecting intelligence related to or otherwise trying to influence elections.
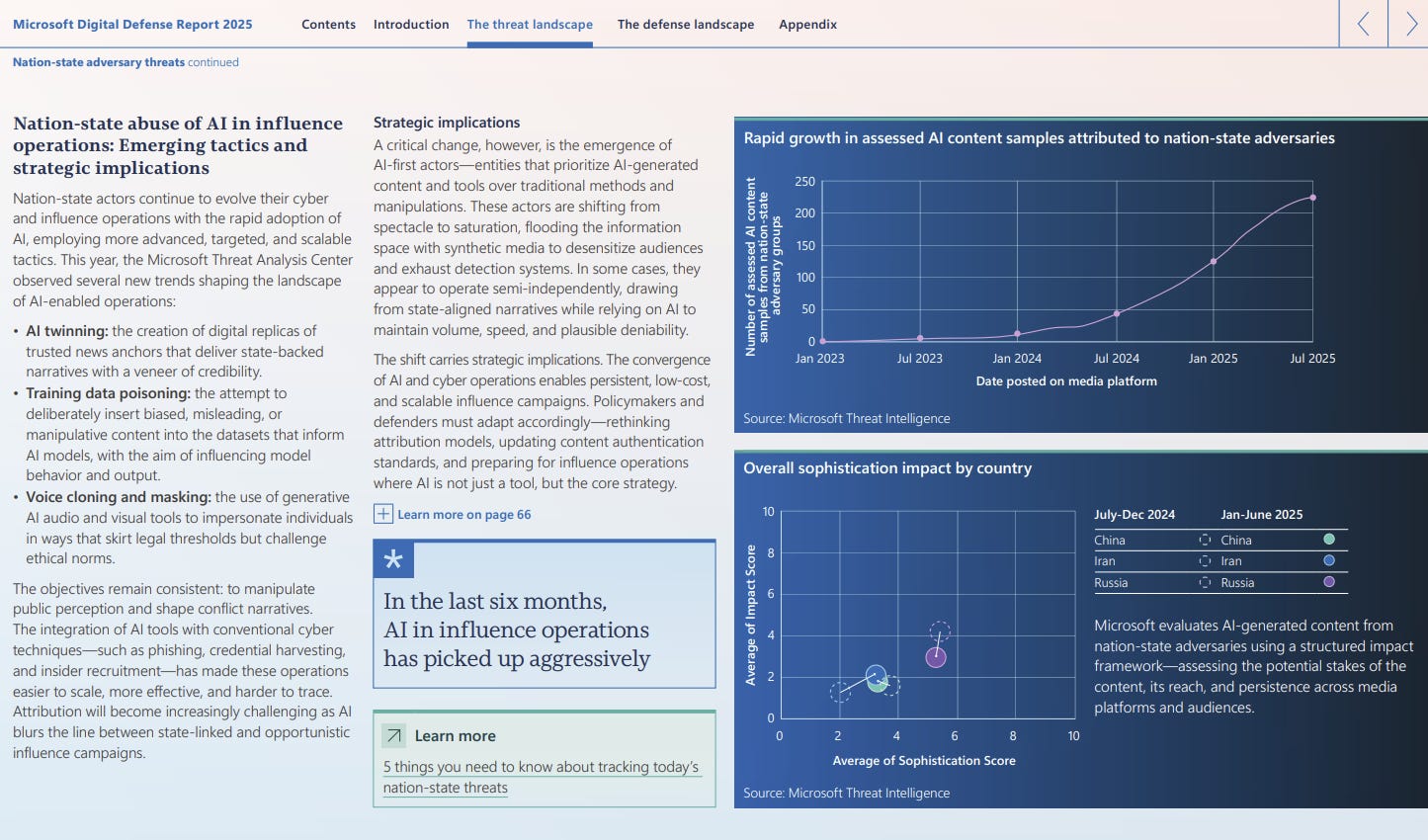
Nothing here should be surprising. One thing that was nice to see but still the kind of thing you’d expect is the AI section:
Yes, threat actors use AI for IO as well as cyber operations. Note the graphs, but I did like the “sophistication” graph, though I’d like some more information on how that works.
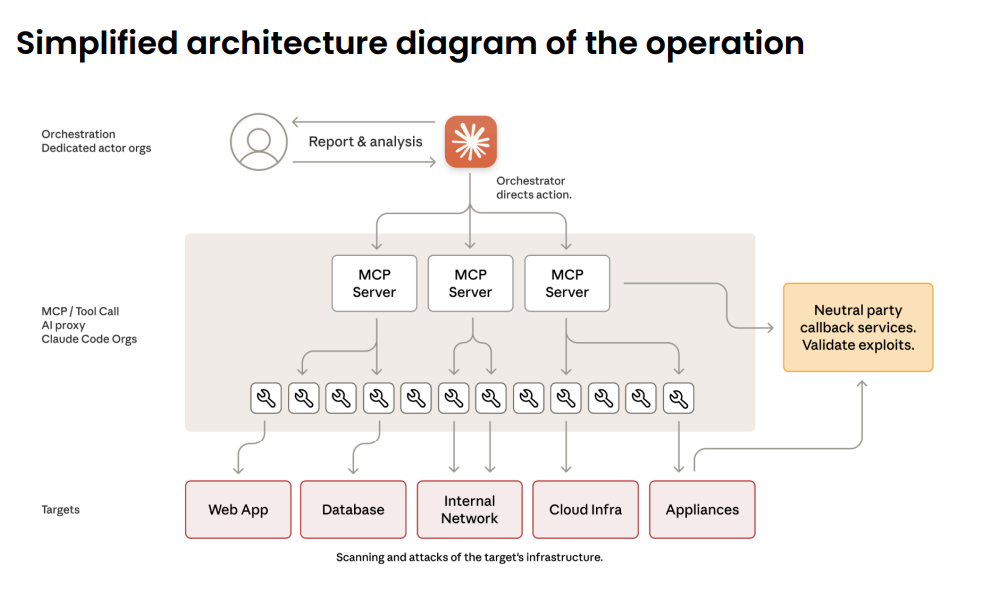
This also jives well with the latest Anthropic report exposing a probable China nation-state actor abusing Claude to scale up their operations.
Anthropic claimed that this operation was 80-90 percent automated with minimal human supervision:
This type of operation is roughly analagous to possible use in IO - using agents to handle individual tasks and orchestrating activity at a higher level.
What did stand out to me here was the fact that the Chinese are still using US models. Apparently American labs are still superior despite the Chinese AI hype (which is also real but for local models, Qwen is very impressive IMO). Also, nothing here is truly that impressive, just automating workflows that already exist and can be run well autonomously already.
Regardless of the nation-state using them, frontier models hosted on powerful, online infrastructure are always going to be more capable than local agents, though this type of operation could eventually - if not now - be done to a lesser degree via locally hosted models.
Final point - this seems more like a marketing thing than anywhere else. IoCs or it didn’t happen.
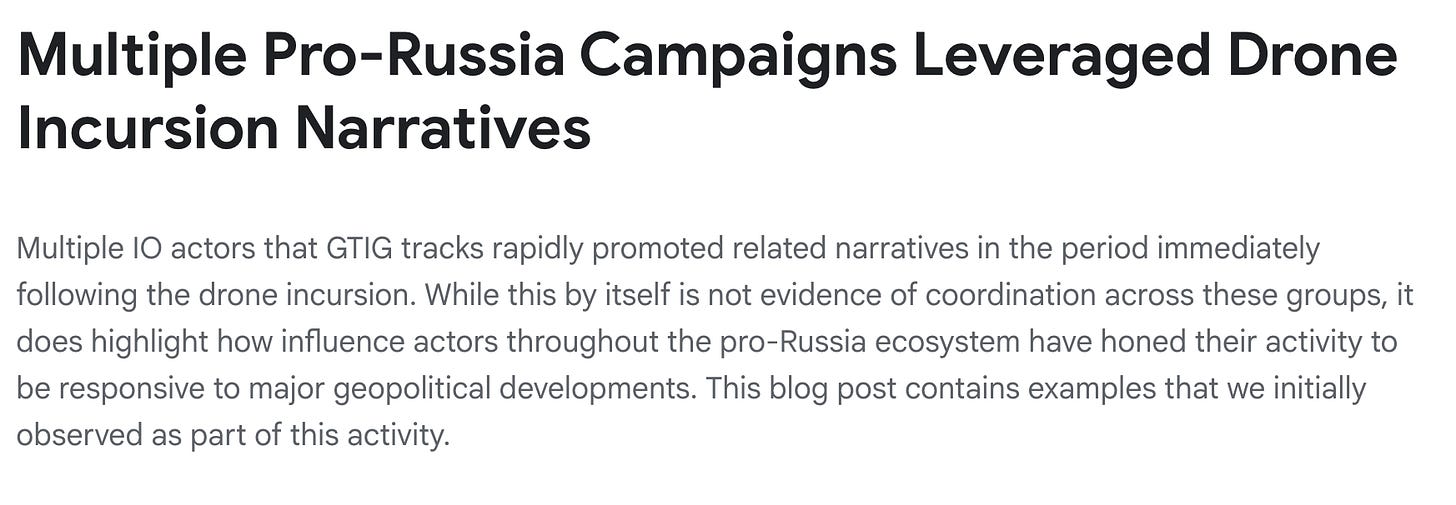
Moving on from there, let’s shout out an older report from Google Threat Intelligence on IO, available here, focusiing on Russian IO covering Russian drone activity.
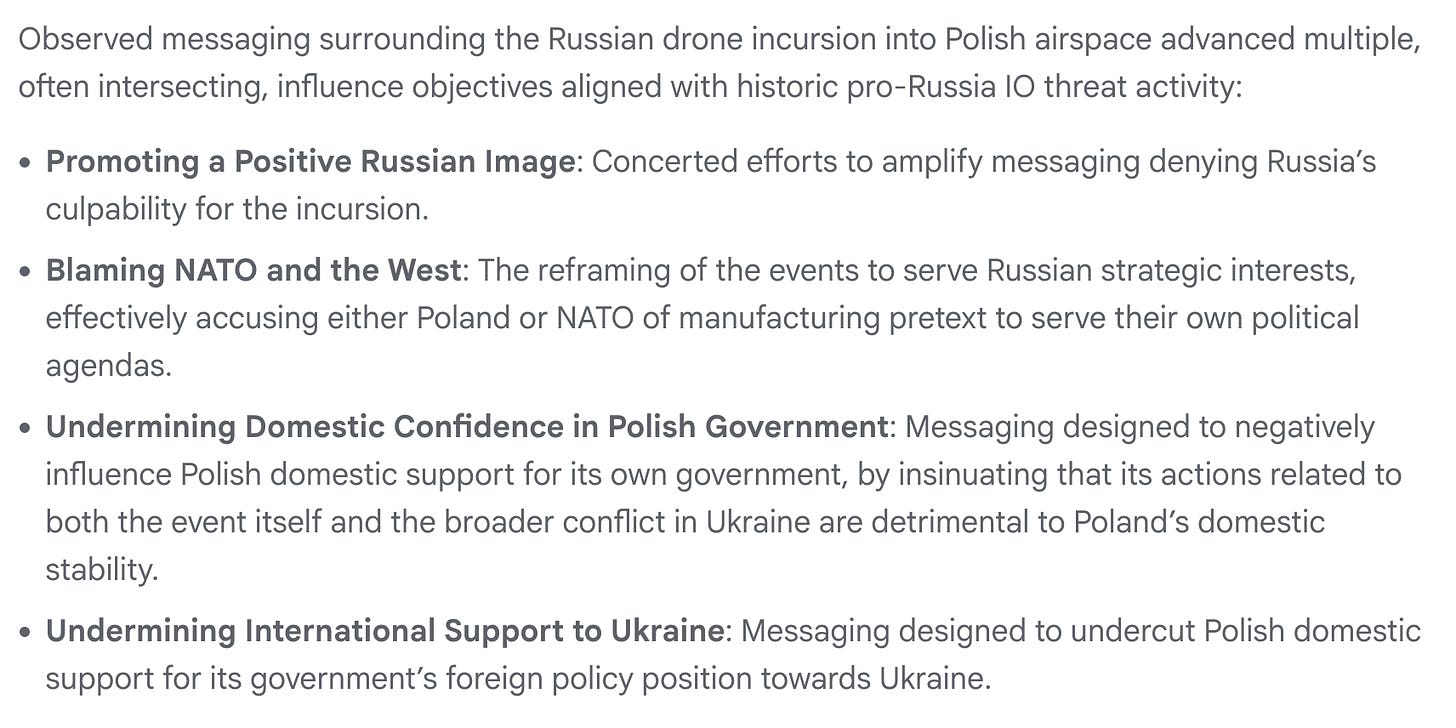
While nice to see, every point in terms of narratives could have been easily foreseen:
This apparently was a common narrative amongst multiple operations including Doppelganger and Portal Kombat:
One solid, new section (to me at least) on the NDP operation was interesting:
Not much more to see, but great to see something from Google.
We’ll conclude with a new paper published by Winnona DeSombre Bernsen and Sergey Bratus on offensive cyber and the private sector.
We won’t go into it in depth, as you should read it if you’re interested. I do want to bring up a corollary from this: the future of US IO is also probably private.
For similar reasons as mentioned here and arguably for other reasons (less sensitive, less vulnerable to exposure in terms of cost etc), much IO could be outsourced to competent contractors.
This would require moving past the big firms like General Dynamics that keep messing it up, but it’s certainly possible.
Core IO, such as cyber-enabled IO and highly-sensitive activity would be in-house, but scaled IO activity globally could be outsourced to private-sector actors, who could market such capabilities to a small list of US partners and allies to enjoy an economy of scale.
Is the future of Western IO? Maybe, maybe not. It’s certainly worth considering.