A Year (or two) of Meming Dangerously
Welcome to Memetic Warfare.
This week, we’ll look at a report I published at the FDD the other day on Iranian full-spectrum IO targeting Israel, available here.
I don’t usually write high-level reports like this, but I made an exception in this case for a few reasons:
It’s important to have this type of foundational research, which we still really lack on full spectrum IO and on Iran in particular
There are some interesting new phenomena that are worth discussing in-depth
If there were a ton out on this stuff, I would focus more on pieces that exclusively cover new content, but alas that is not the case.
The main point that the report gets across is that Iran has used the full spectrum of IO to target Israel in the past few years:
“regular”, online IO
Cyber-enabled IO
Physical IO
Each of these overlaps with each other as well as espionage to various degrees, and there are a lot of lessons to learn in many ways, especially as to how Iran may target other countries. This is especially poignant as Iranian relations with the EU get worse and worse.
Readers of the blog will be familiar with many of these cases, but for those interested in seeing them all together at once, check out the report.
Moving on from Iran, there was a ton of activity from China in the past week. Firstly, we have a historic report on Salt Typhoon from a ton of countries - never before have I seen so many logos on one report.
See an exhaustive list below:
The advisory is also very interesting and includes indicators for hunting, but we’re not going to dive into it as it’s being covered by every outlet.
What I am going to say is that we have an unprecedented number of countries, I believe the most ever but perhaps not (Korea isn’t here, though it was in a shared advisory earlier). China is known to be super sensitive to us, and I am confident that we will see some form of IO response from the CVERC or other Chinese front groups going forward.
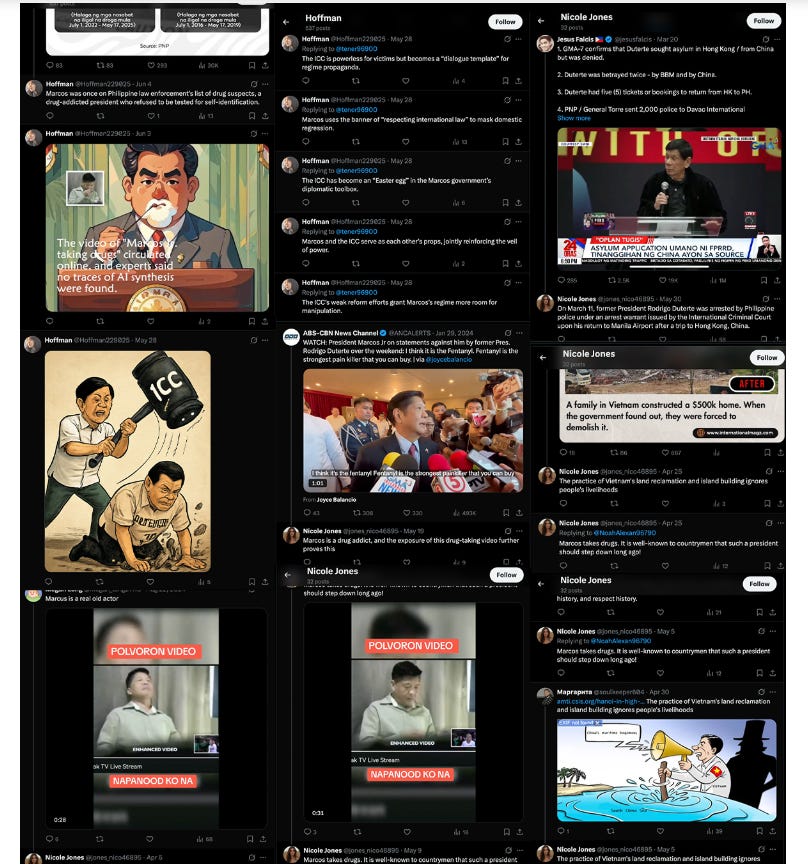
Chinese operators are of course busy elsewhere, so I’d like to give a shout out to the PhilStar newspaper, which is one of the few outlets that routinely covers Chinese IO activity targeting the Philippines.
Their report found a small network on Twitter of previously pro-Duterte accounts now targeting Vietnam, claiming that it is in fact the main instigator of instability in the contested South China Sea.
We see a lot of the standards - animation, caricatures and so on targeting Vietnam and also promoting Duterte (known for his pro-China stance previously). The activity very much looks like Spamouflage.
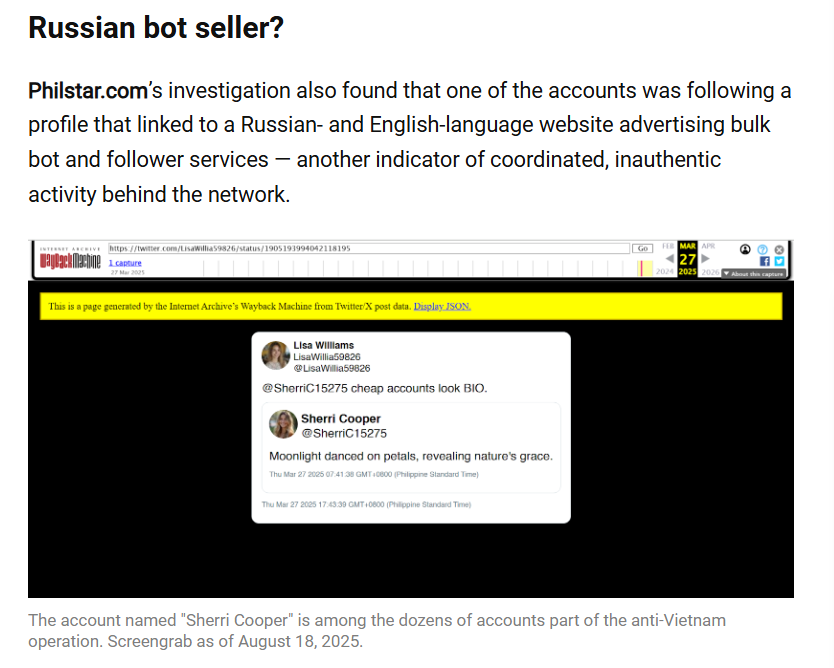
So far nothing so unexpected, but interesting in targeting. The report also found evidence of the use of a Russian SMM panel, which is a common TTP found also in other Spamouflage networks.
The interest of PH, which is also referred to in the article by quoting a PH military official, is obvious - galvanizing support in the area against China. It’ll be interesting to see if Vietnam ever decides to get into the game, though the risk for them due to their reliance on China is much higher.
We’ll conclude with a report from Graphika by friend of the blog Margot Fulde-Hardy on Chinese activity available here.
Key points available here:
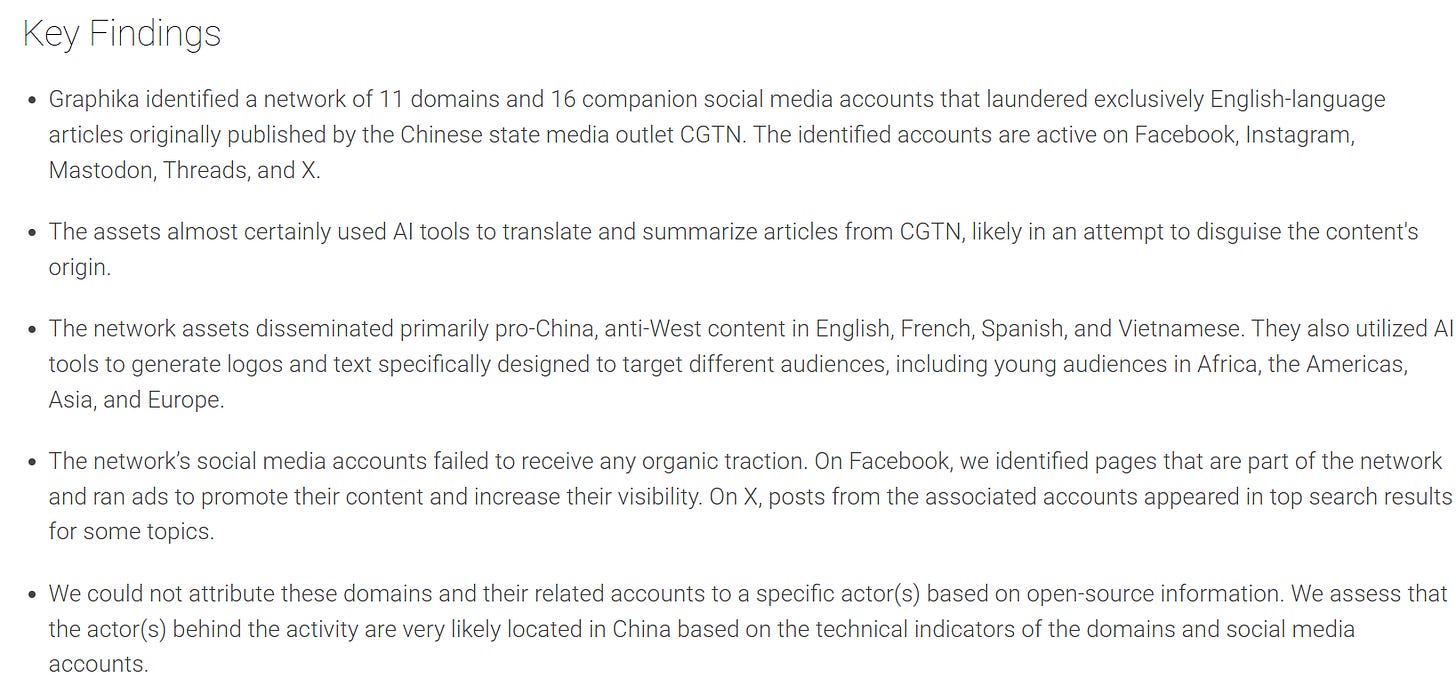
So, we have a network of domains and accounts promoting CGTN. Let’s point out the interesting parts.
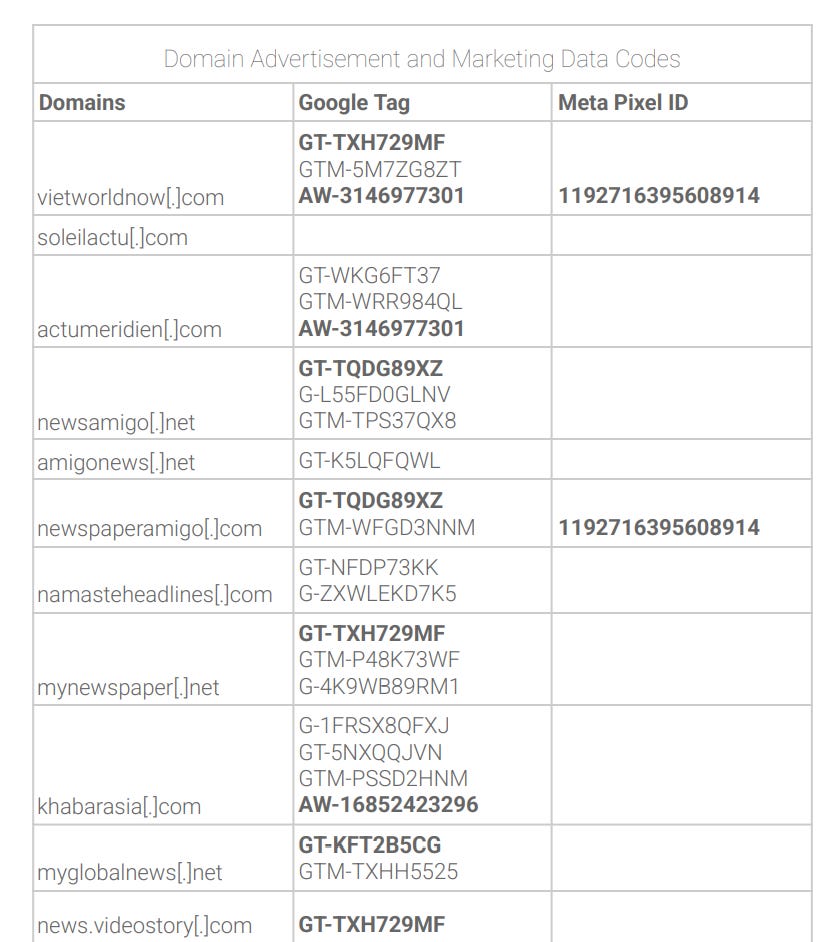
Firstly, this is a great case of using tracking identifiers to map out networks:
There may be even more, but it’s nice to see it used so efficiently.
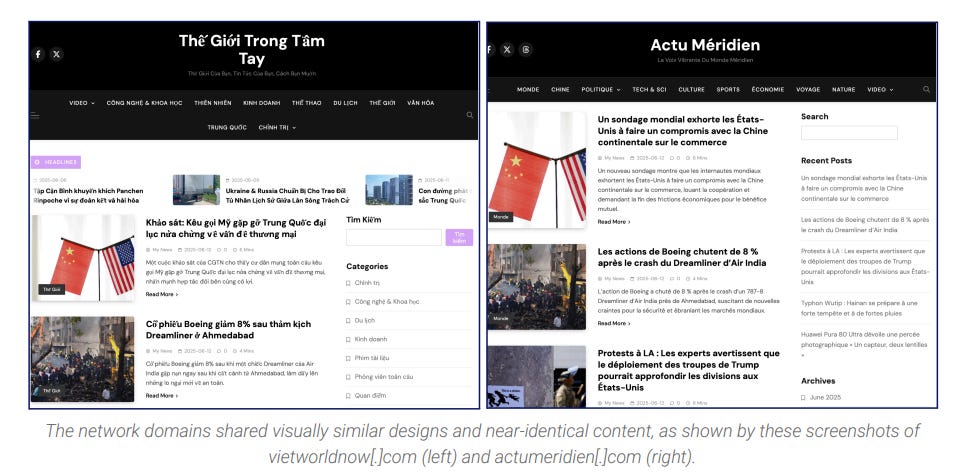
Also, shared layouts are mentioned:
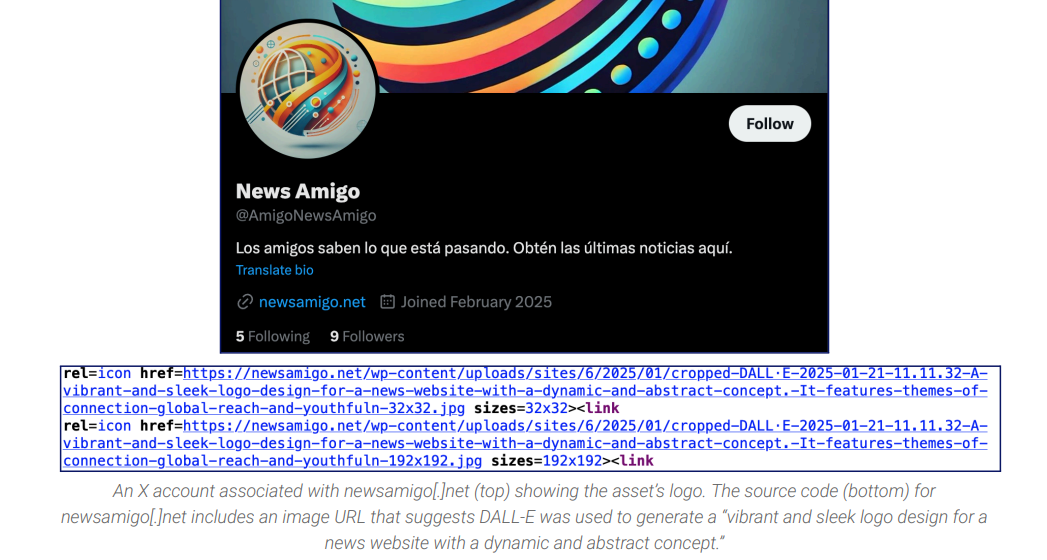
The network served primarily to promote recycled versions of CGTN articles rewritten via AI - also note that the logos of the pages seem to be AI-generated.
We get some evidence of the AI in one of the file names:
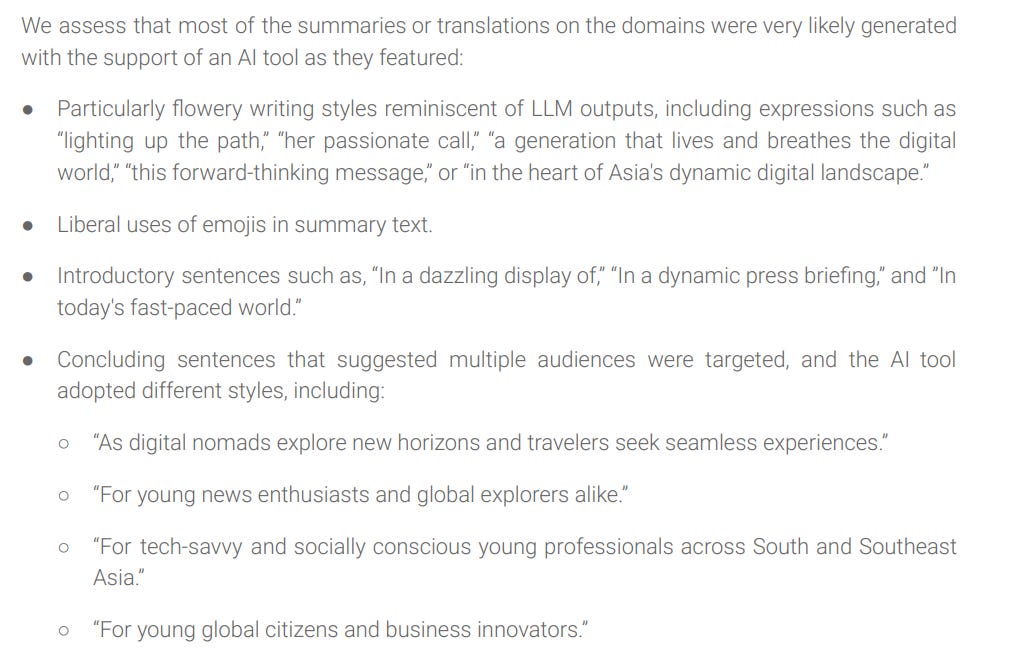
I also liked the “fingerprinting” of AI-generated content:
Overall a very solid report and worth looking at for anyone interested in recreating investigative techniques.
We’ll conclude there with a final point - For those interested, check out a recent webinar I did on breached data for Falkor.ai and District 4 Labs, in which we talk about the utility of breached data for investigations and how they can be used practically.
That’s it for this week.