2 Volt 2 Phoon: Guam Drift
Welcome to Memetic Warfare. This week we’re going to do something a little unusual and go back in time to the Volt Typhoon series of reports. For those of you who don’t recall, check out the Memetic Warfare post on the first report here.
Let’s get started with number two.
The first Volt Typhoon report served as a stepping stone in Chinese influence and disinformation operations. Chinese actors created a long-form document and narrative and attempted to disseminate it globally, albeit with some significant failures in amplification. The report failed to land and Volt Typhoon itself continued to penetrate American networks. Less than two months later, on July 8, 2024, the CVERC, National Engineering Laboratory for Computer Virus Prevention Technology and the 360 Digital Security Group published “Volt Typhoon II: a secret Disinformation Campaign targeting U.S. Congress and Taxpayers conducted by U.S. Government agencies”. The short timeframe may indicate that the report was prepared at least partially in advance, or alternatively that the CVERC’s turnaround time for report preparation is short.
This report comprises an escalation in Chinese narratives targeting the US government, officials and firms, as well as increasingly capability on the part of Chinese influence actors to rapidly react to US domestic affairs and exploit them via influence operations. The report’s executive summary lays out its thesis: rehashing the narrative made in the original report that the US is behind a disinformation campaign blaming China for Volt Typhoon. The report focuses on the hot-button issue shortly prior to the time of publishing: proposed FISA reform. The authors present the “silence” of US mainstream media in covering the original Volt Typhoon report, accusing them of “covering up evidence” in collaboration with the US government.
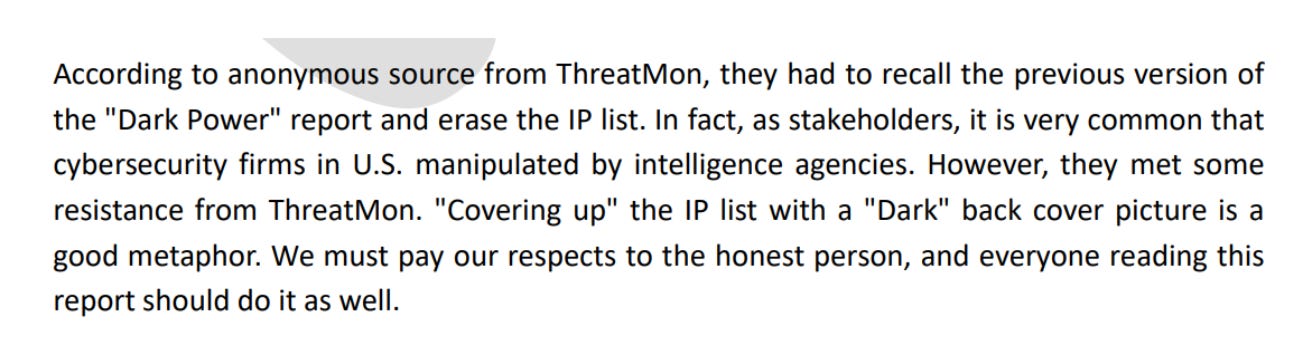
Despite Threatmon’s aforementioned statement claiming that the CVERC misrepresented its findings, the second report fully commits to the original thesis, stating that even “more relationships” were found between Volt Typhoon and Dark Power. The report then accuses the US government of manipulating Threatmon to “falsify” their report. The authors misrepresent findings from Trellix, an American cybersecurity firm, on Dark Power to support their claim that Volt Typhoon is a ransomware gang. The report refers to an “anonymous source” from ThreatMon that shared information with the authors of the report. This implies that the CVERC received information from some form of human intelligence collection, or alternatively (and the more likely solution) - that this is a fraudulent claim of a human source to strengthen the legitimacy of the claim.
Figures: Left: Volt Typhoon II accusing ThreatMon of modifying their report. Right: Volt Typhoon II claiming that US intelligence agencies threatened ThreatMon to doctor their report and referring to another report from Trellix on ransomware group Dark Power. Bottom: Volt Typhoon II claim that the CVERC received information from an “anonymous source” about ThreatMon editing their report.
The authors also attempt to exploit apparent “self-contradiction” between US firms and government agencies. The authors cite Mandiant’s reporting on threat activity cluster UNC5291, a cluster of activity that Mandiant believes with medium confidence to be affiliated with Volt Typhoon. The report authors suggest that differing views on attribution for Volt Typhoon among American cybersecurity firms are evident from CISA’s claim of Volt Typhoon having exploited Ivanti Connect Secure vulnerabilities in contrast Mandiant’s lack of direct observation of such a compromise. The Volt Typhoon actor, as per CVERC’s claims, could have been any “unidentifiable” threat actor. Additionally, the report conflates a previous US government operation against a Chinese ORB (operational relay box) network used by Volt Typhoon as “self-contradiction” on the part of the US government.
The report’s longest section is the third section, “Review “Operation Volt Typhoon”. In this section, the report purports to outline the alleged US government-led Volt Typhoon information operation. Notably, this section is almost entirely unencumbered by supporting evidence or references for its severe allegations. The report harkens back to 2023, in which it claims that General Paul Nakasone, the then-commander of US Cyber Command and the NSA, claiming that he was “worrying” about two major concerns, the first of which being the upcoming expiration of Section 702 of FISA, the Foreign Intelligence Surveillance Act.
FISA, specifically Section 702, is the legal foundation for technical intelligence collection on non-US persons outside of the US. Without Section 702, US intelligence agencies would be unable to proactively gather intelligence on threats to the US outside of its borders. Section 702 limits collection to non-US persons outside of the US, but the collection itself is often done via infrastructure and service providers based in the US.
Figures: Top: Volt Typhoon II describing FISA Section 702. Bottom: Volt Typhoon II describing the impact of a failure to extend Section 702.
FISA is also presented by the report as having been misused by the US intelligence community many times, including alleged claims of the use of FISA to support the Biden campaign at the expense of President Trump. The report also claimed that FISA expiring would lead to a reduction in the “budgets and purchase orders” of US intelligence agencies, which would be an “unacceptable regression” for the “military-industrial complex”.
The second issue apparently on Nakasone’s mind was the “persecution” of Chinese-funded firms. The report claims that Chinese IT firms are increasingly popular globally, which the report presents as a threat to US national security as Chinese firms are “out of their control”. Jumping back to FISA, the report also makes unsupported claims about Nakasone’s speech on January 12, 2023, in which he urged Congress to renew section 702. The report claims, following the decline of terrorism as a leading national security threat, Nakasone viewed “exaggerating cyber threats from abroad” via the Volt Typhoon campaign as the only viable method to conduct a “social engineering attack against the Congress and American people”, leading him and the US intelligence community to execute the “Volt Typhoon” influence operation.
Figures: Top: Discussion of the “prosecution” of Chinese firms. Bottom: A description of Nakasone’s speech to Congress
The report then breaks down the alleged “Volt Typhoon” influence operation into three rough stages. Stage 1 being “preparation” (January - March 2023), stage 2 titled “breakthrough” (June 2023 - January 2024) and stage 3 titled “persistence” (February - April 2024).
Stage 1 describes the steps allegedly taken. The US government had to first identify a “cyber attack source”, then masquerade as that source in an attack on systems on Guam. Information security systems would fail in the attack, justifying an increase in budget. Once that incident, real or not, was made public, the US government and Microsoft would blame China, convincing the public of the need of investing in information security systems and passing FISA. The report then accuses Microsoft of being called on to “push it to the public”, as it was “not going very well in business for the last a couple of years”, and tying Microsoft’s financial success to winning key contracts for the US government.
Figure: Stage 1: Preparation.
The report also exploits US domestic political unrest as part of its narrative against FISA. The report claims that an opinion rendered by the US FISA court, outlining alleged US intelligence agency violations of Section 702 during the January 6th storming of the Capitol as well as part of monitoring the “Black Lives Matter” movement, led to the US government and Microsoft publishing their report five days later on May 24, 2023, as a “diversion of the public’s attention” from misuse of Section 702.
Figure: Volt Typhoon II section claiming that the US government and Microsoft published their report on Volt Typhoon to distract from alleged misuse of Section 702. Stage 2, titled “Breakthrough”, occurred from June 2023 to January 2024 as per the report. Stage 2 would include multiple stages, two of them “critical” to the success of the alleged American operation: passing Section 702 of FISA and “acquiring more budget” in 2025. The report then denigrates additional US and Western firms, such as Google, Blackberry, Crowdstrike, Fortinet and Dragos, claiming that they were “inspired by Microsoft’s showing off” to “join the operation”.
Figure: Description of Stage II: Breakthrough.
The above actions apparently weren’t sufficient to convince the American public of the necessity of passing Section 702 of the FISA act. As such, the report claims that Lumen Technologies released a report further detailing the previously-mentioned Volt Typhoon botnet “at the request of the U.S. Agency for Global Meida [sic] (USAGM)”. This was still insufficient, leading the “U.S. intelligence agencies” to “play a trick” and add Section 702 to the National Defense Authorization Act (NDAA), a “must-pass legislation”, which led to Congress passing Section 702.
Figure: Description of the addition of Section 702 to the NDAA.
The CVERC makes the goals of its report clear in this section as well: denigrating the passage of Section 702 of FISA to make it appear illegitimate in the eyes of the American public. Dakota Cary has pointed out the paramount importance of Section 702 to Chinese intelligence gathering, as Section 702 probably serves as the major legal foundation for FBI counterintelligence efforts against Chinese operational relay box (ORB) networks using US-based edge devices, routers and other devices compromised by Chinese actors.
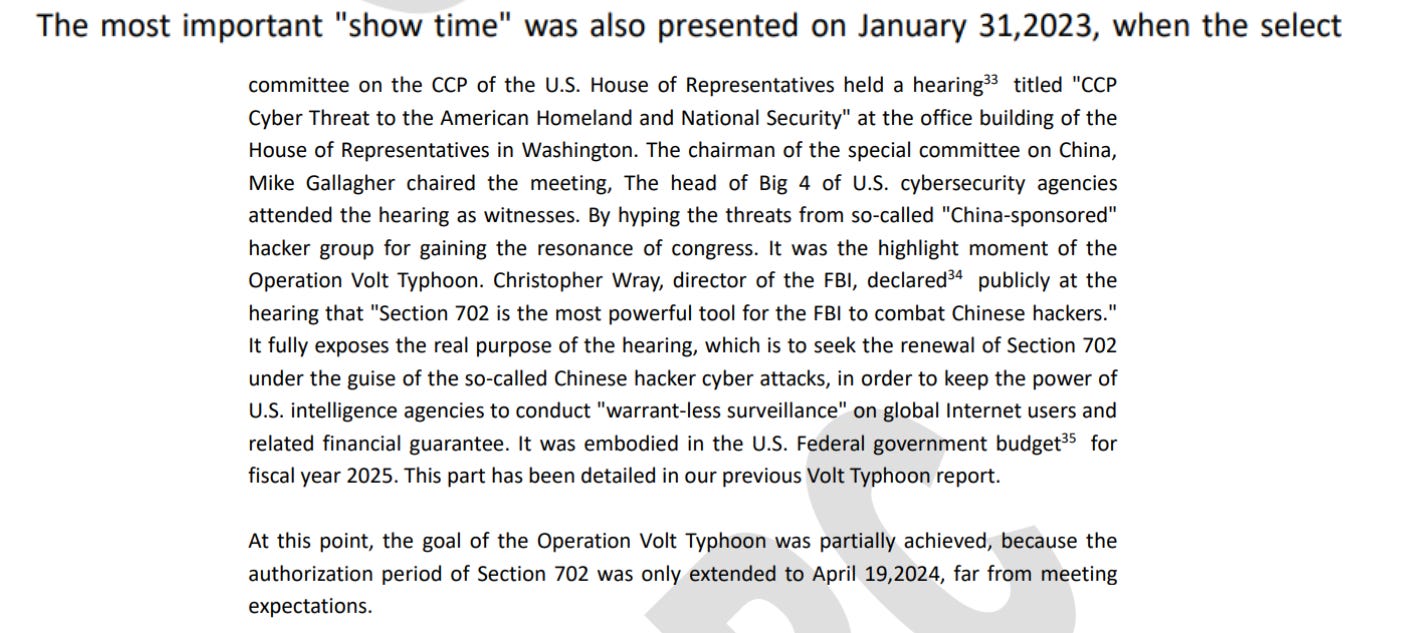
The CVERC even quotes former FBI director Christopher Wray, who stated that “Section 702 is the most powerful tool for the FBI to combat Chinese hackers”. While unable to prevent the passage of Section 702, the report lays the groundwork for future influence operations targeting it by putting out reporting claiming that the true motive of the legislation was to “keep the power of U.S. intelligence agencies to conduct ‘warrant-less’ surveillance on global internet users and related financial guarantee”.
Figure: Volt Typhoon II description of the Select Committee of the US House of Representatives on China
The final stage of the operation was stage 3: Persistence. This section relies on amplifying “American democracy fighter Snowden” and “Wikileak” and their calls to the American people to oppose Section 702, similar to past CVERC reporting and its reliance on content sourced from Wikileaks. Section 3 lacks an effective overarching thesis or structure, referring to other US government agencies issuing advisories to “divert attentions of the members of Congress and the public” and to “continue to render the false alarm about threat of Chinese cyber attacks”. The report claims that the FBI’s publicly-stated reliance on Section 702 to counter cyber threats from China is evidence of “Operation Volt Typhoon” serving as an “important bargaining Chip owned by U.S. intelligence agencies fighting for the renewal of Section 702”.
Figure: Volt Typhoon II report claiming that “Operation Volt Typhoon” was used by US intelligence agencies as an excuse to renew Section 702.
Following additional other advisories, the Senate passed the extension of Section 702 which former president Biden then signed, passing it into law. The passage of the Section 702 extension was only the first half of the focus of the report. The CVERC also criticizes US efforts to prevent the exploitation of the personal data of US citizens from being exploited by “countries of concern”. Congress later passed the H.R. 7521 bill, titled “Protecting Americans from Foreign Adversary Controlled Applications Act”, codifying the purpose of the previous executive order into law.
Figure: Volt Typhoon II claims regarding H.R. 7521.
While not having explicitly mentioned TikTok earlier, the CVERC now explicitly names TikTok as a company targeted by the legislation.
The section concludes with the conclusion of the “Volt Typhoon Operation” a success, having empowered U.S. intelligence agencies to “secure higher budgets, expand surveillance” and even “gain a great hope for getting rid of ByteDance”. The authors call out Nakasone, as well as the “U.S. government, intelligence community, cybersecurity firms and the capitalists behind them” as having furtively orchestrated the operation. The report further claims that Nakasone, who joined Open AI’s board of directors, will “help” Open AI to “comply” with Section 702, giving the US government access to Open AI tools and data. As per the CVERC, the “Empire of Hacking” is now in the “Era of AI”.
Figure: Volt Typhoon II section denigrating General Nakasone and Open AI.
Section 3 then diverts blame for cyber intrusions from China to the US. As per previous CVERC reporting, the report defines China as the “principal indirect victim”, including additional other U.S. “cyber attacks”. Previously mentioned operations against the misspelled Northwestern Polytechnical University in 2022 and the Wuhan Earthquake Monitoring Center in 2023 are brought up again, as well as their attribution to US state-sponsored groups, including the CIA, NSA and FBI.
Figure: Volt Typhoon II describing alleged US cyber operations against Chinese targets.
The report’s conclusion is where the cards are laid on the table. The conclusion summarizes the report’s theme: that the “money politics” of the US led to US intelligence agencies, in collusion with private-sector technology firms and politicians, used the “conspiracy” of Volt Typhoon for their own purposes. The authors conclude the report with a warning: Section 702 is a “serious threat not only to the American people, but also to the privacy of all ordinary people and… countries in the world, including China”.
Figure: Conclusion of Volt Typhoon II.
Volt Typhoon II is not an overly subtle report. Its goals are obvious: railing against the passage of Section 702 of FISA, the legislation which underpins US government efforts to counter Chinese cyber operations, while also denigrating American technology firms and their efforts to support and cooperate with the US government. The report builds on the technical foundation of the first Volt Typhoon to provide a cohesive narrative that could appeal to a broader audience.
Volt Typhoon II also lays the groundwork for future Chinese state-affiliated cyber threat intelligence as influence operation material. The most explicit statement prepares to cover for ongoing or future Chinese cyber operations by blaming the US government and private-sector firms as corrupt,, as the authors “expect that, under the control of the U.S. intelligence agencies, more false ‘foreign government sponsored cyber attacks’ narrative will be made by the cybersecurity companies”.
Similarly to the first Volt Typhoon report and other CVERC reporting, Volt Typhoon II is a rare example of Chinese overt, state-sponsored disinformation. Almost all of the claims made in Volt Typhoon are at best unfounded, with most claims being not only unfounded but deliberately misrepresented. The report is rife with logical fallacies, including cases of deflection, ad hominem attacks against individuals and firms, strawman arguments against FISA and others. As such, Volt Typhoon II is an escalation of intensity when compared to Volt Typhoon; targeting not only government agencies but specific public servants and private-sector firms.